(ISC)2 Singapore Chapter LearningNeverStops Virtual Sharing on 11 May 2022:
Webinar Topic: Zero-day RCE Vulnerability Spring4Shell: What Does It Mean In Cloud Native?
Speaker: Stan Hoe, Solution Architect APJ, Aqua Security
In the recent years, Cloud Native has become the preferred approach for application development due to the benefits that it brings, e.g. highly scalable, agile, and predictable.
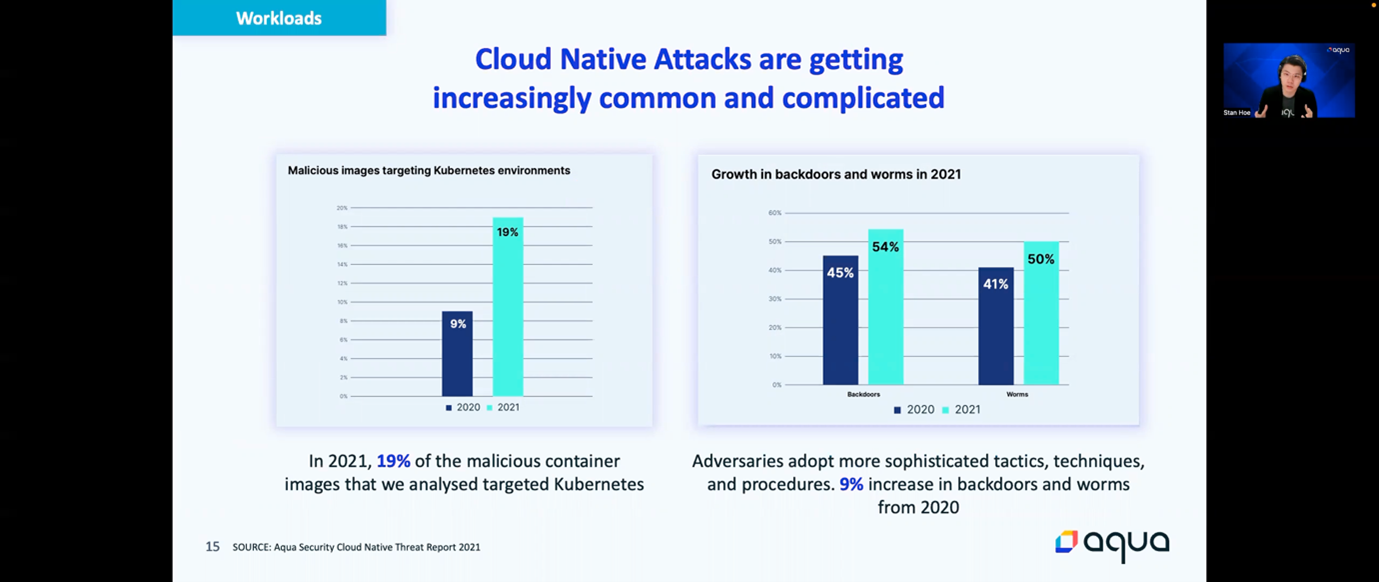
As Cloud Native continues to gain widespread adoption, adversaries recognize this and are starting to shift their focus. As a result, Cloud Native attacks that targeted containers and Kubernetes are rapidly increasing in prevalence and becoming more sophisticated:
- Better hiding the attack (fileless malware, packed files, etc.)
- Better persistency (rootkits)
- Privilege escalation (container escape)
- Hiding a more sinister impact (data exfiltration, credentials theft, backdoors, malware deployments)
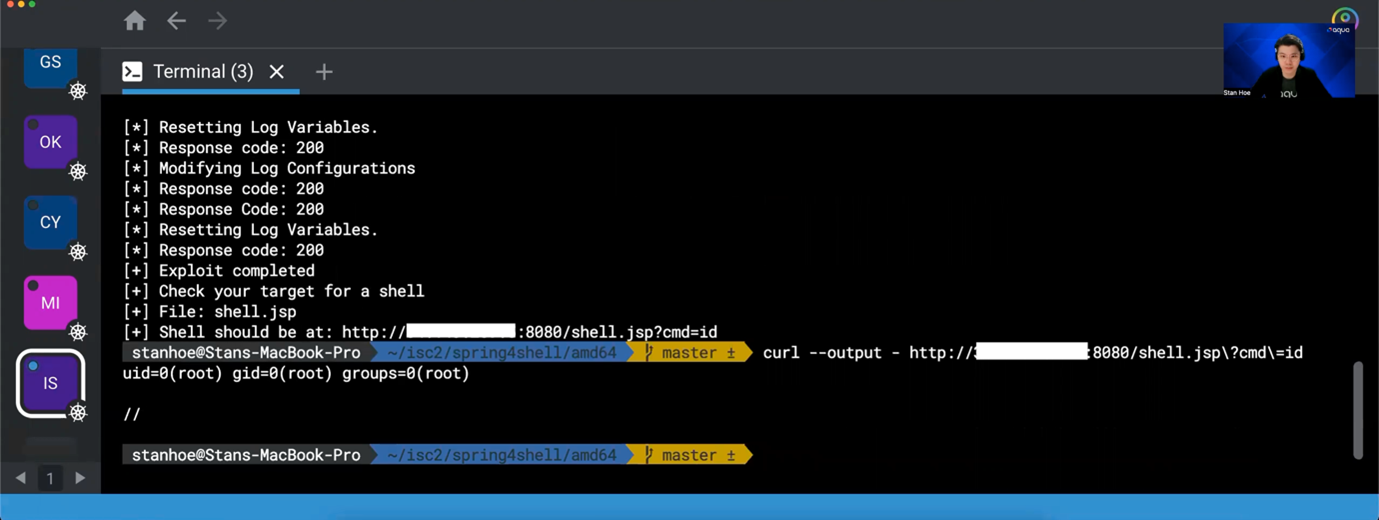
In fact, container image vulnerability (including supply-chain attacks) is just one of the possible attack surfaces that an adversary can utilize to infiltrate a cloud native environment. An adversary can also gain initial access into your environment through misconfigurations that exist in your Kubernetes cluster or by exploiting your vulnerable container. For example, a container that is vulnerable to the Spring4Shell vulnerability (CVE-2022-22965) allows an adversary to easily perform remote code execution through a java web shell spawned from the exploit. As a result, a malicious payload/script will then be downloaded and executed in the container for the adversary to execute further attacks.
However, this can be prevented by enforcing container immutability with technologies such as Drift Prevention. By ensuring that the state of the container reconcile with the image that they are based on, we will be able to prevent any malicious payloads from being executed as inorganic executables will be blocked.
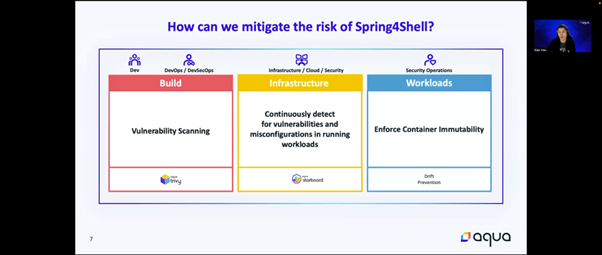
In summary, it is important to integrate security into the entire Cloud Native lifecycle:
- Build – Perform image vulnerability scanning to detect for vulnerabilities and mitigate them before deploying them as containers
- Infrastructure – Gain continuous visibility into the misconfigurations and vulnerable workloads that exist in the environment
- Workloads – Enforce container immutability to protect against zero-day vulnerabilities /attacks
(ISC)2 Singapore Chapter LearningNeverStops Virtual Sharing on 12 April 2022:
Webinar Topic : Unhackable? Lessons in Defensive Coding from Hacking Synology Network Attached Storage devices
Speaker: Eugene Lim & Loke Hui Yi
One of the rare events where we are having 2 distinguished speakers who are renowned in the industry. Both of them believe "hack for good" , regularly participate in live hacking events and won multiple awards from the competitions. From Amazon to Zoom, they have assisted many enterprises to secure their products by uncovering many range of zero day vulnerabilities.
The presentation begins by illustrating one of the recent bug bounty programs that they have participated and shared across what has been identified, how was it being discovered and what are the lessons can be applied to secure the software.
They have shared that although no software can be truly declared “unhackable”, there are several defensive coding techniques teams can be implement to limit the impact of individual vulnerabilities:
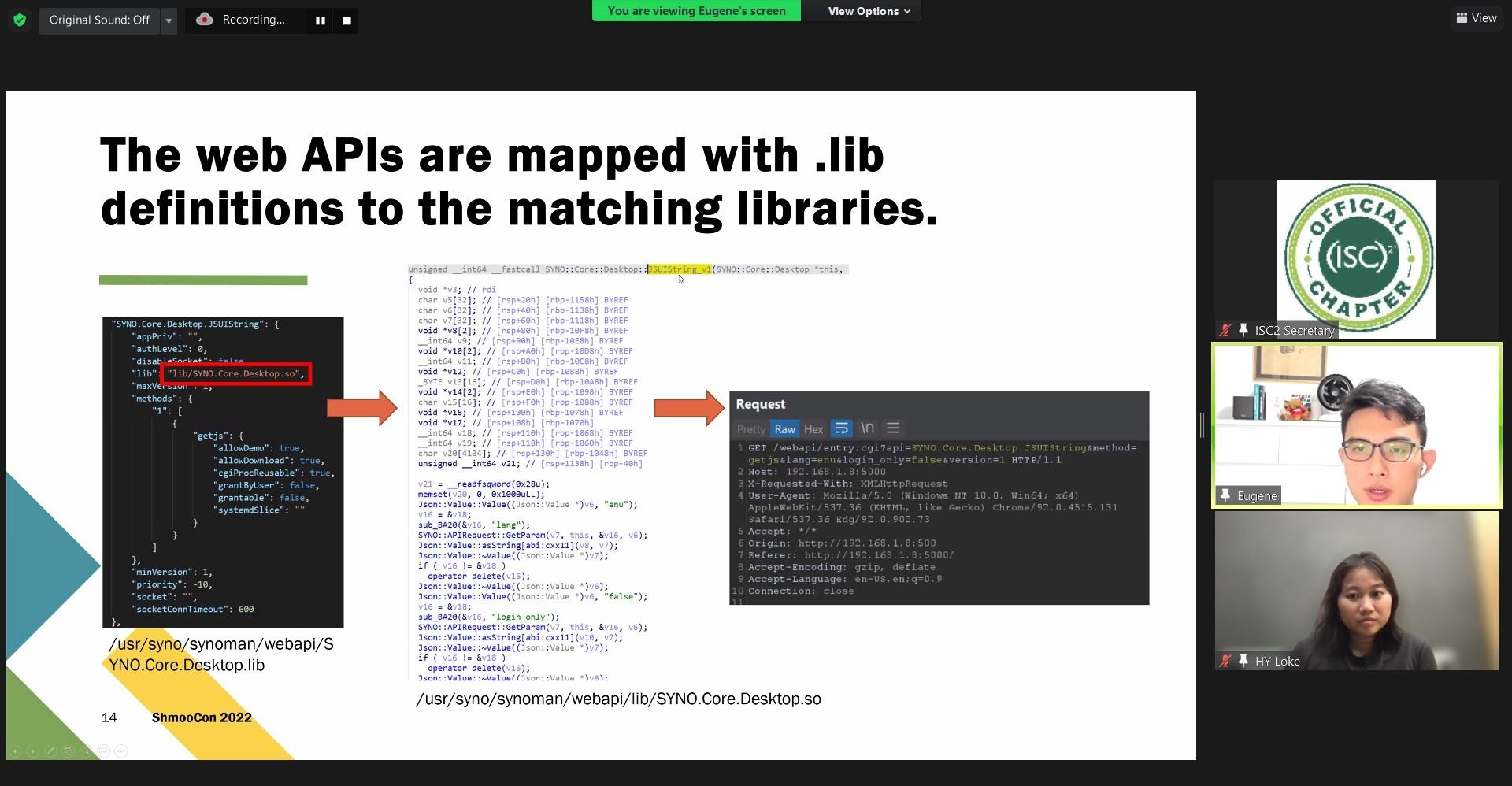
Apply declarative authentication and authorization, funnel to a single source of truth, and minimize the attack surface to authenticated APIs. This reduces the vectors of unauthenticated exploits and simplifies authentication and authorization.
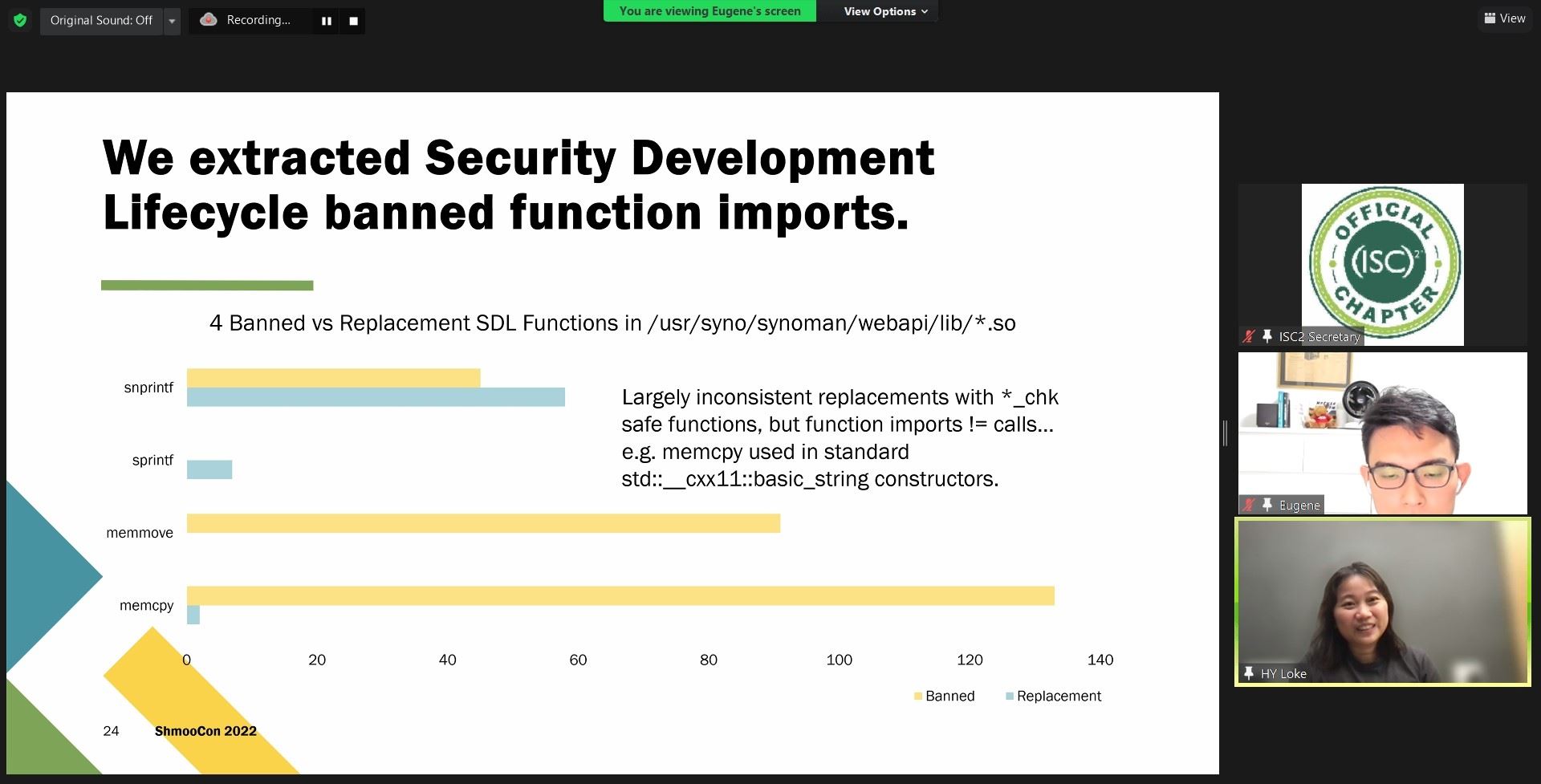
Replace memory-related standard library calls with their hardened equivalents or use code-scanning tools to enforce safe usage. Despite the advancements in software frameworks, memory corruption vulnerabilities are still being exploited and short-circuit application security.
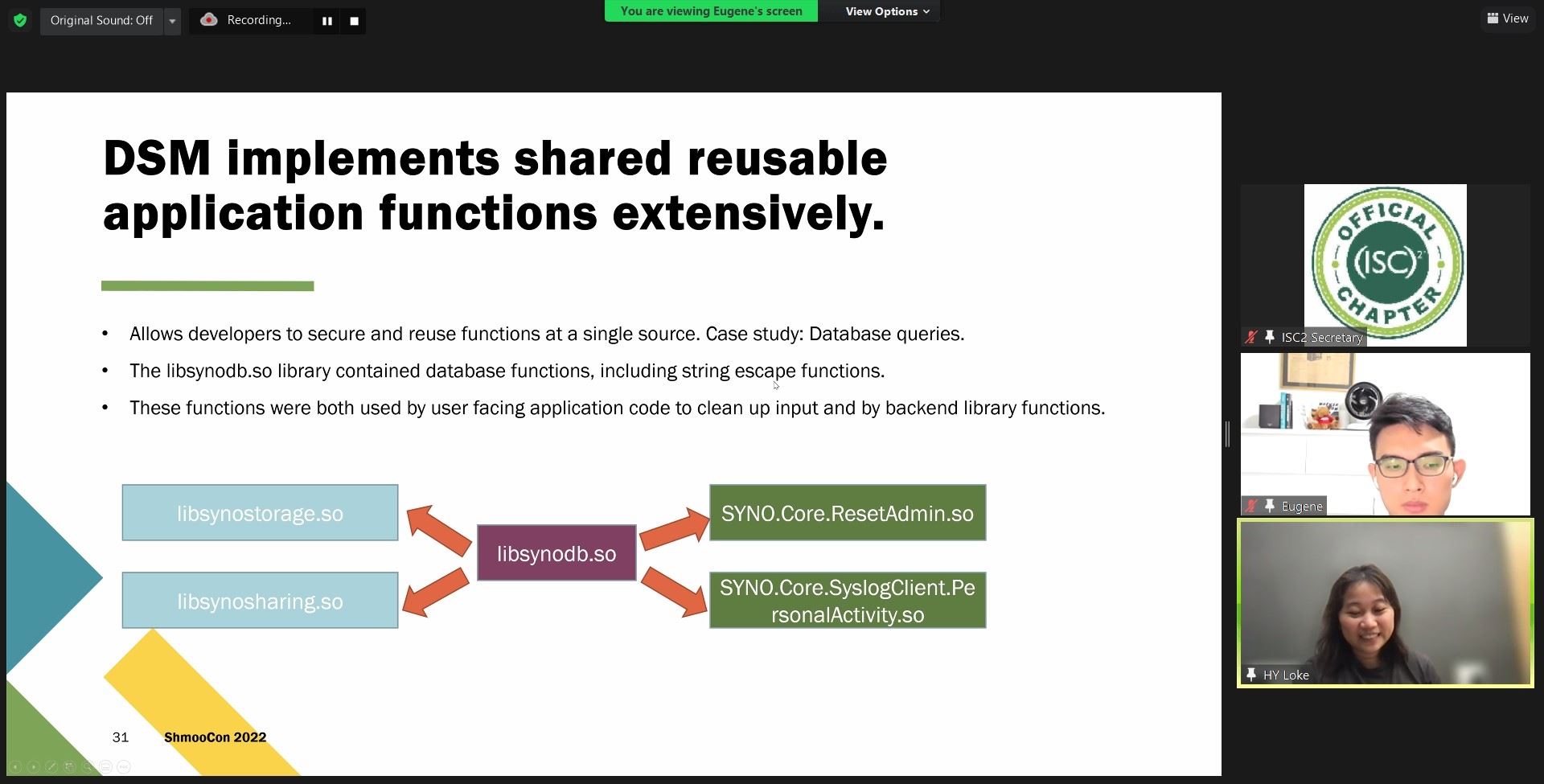
Implement critical or sensitive functions securely in a library and practice discipline in using them. Patches will be able to address vulnerabilities across-the-board rather than at individual sources and sinks.
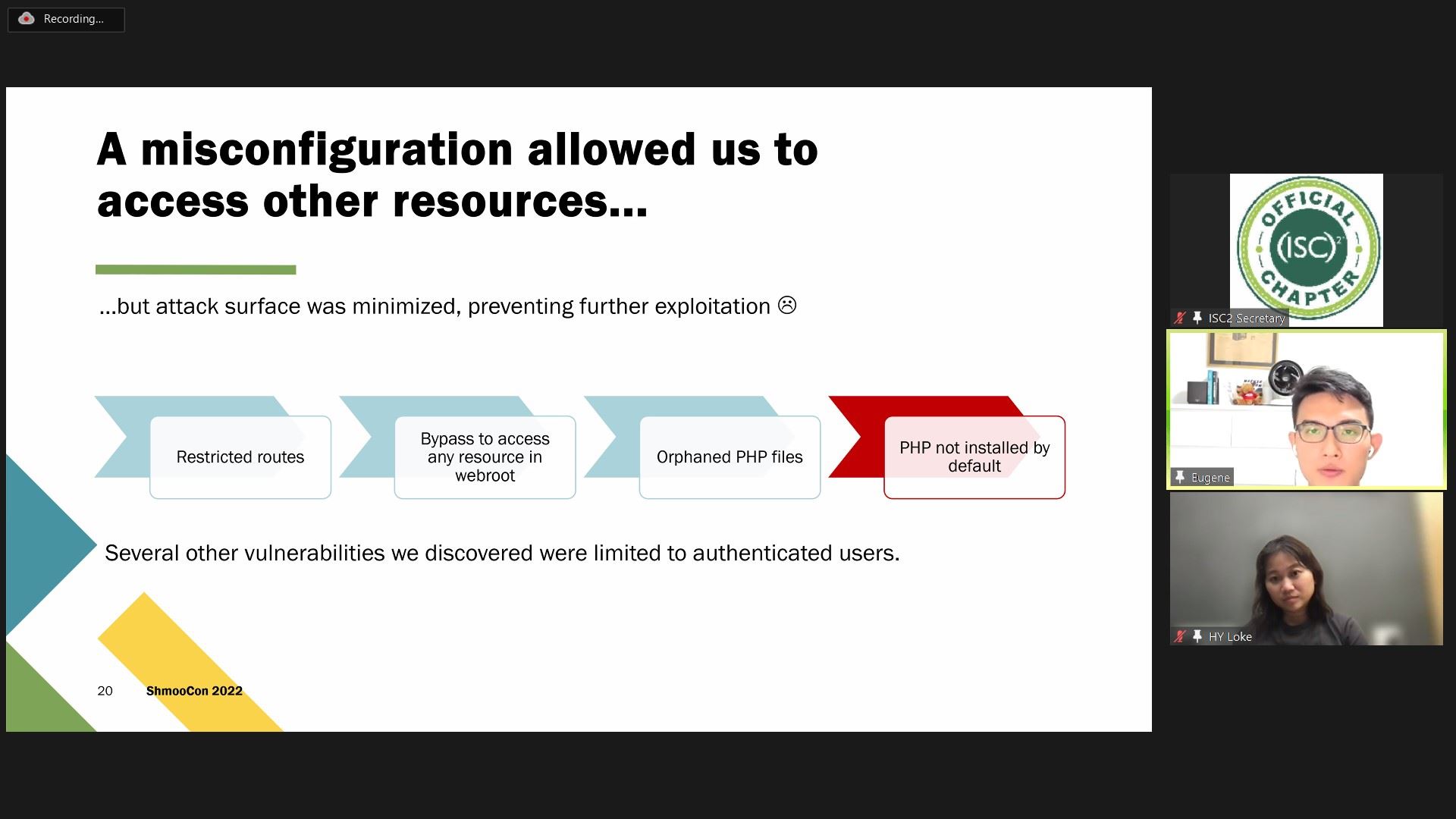
More features doesn’t always have to mean a proportionally larger attack surface. Attackers seek the low-hanging fruit and move on to simpler targets.
Through the post event survey's feedback, we have received encouragement from local chapter members to conduct similar session with local talents embracing our seminar. Thank you all for participating. Join us at our next LearningNeverStops event.
(ISC)2 Singapore Chapter LearningNeverStops Virtual Sharing on 16 Feb 2022:
Webinar Topic: Enterprise Risk Management Strategy for the Next Era
Speaker: Alan Ng

There will always be weakness and flaws in the human element, system, operational environments and supply chains that adversaries will be able to exploit, sometimes with little effort or low complexity techniques or tactics.
More and more organization embark on digital transformation and adoption of new technologies such as cloud, AI/ML, IoT and maybe even blockchain, 5G or quantum computing. Such proliferation of new technology introduces new cyber risks and opportunity to allow adversaries to exploit vulnerabilities against people and organizations through technology.
Likewise, cybercriminal and adversaries are also transforming and more agile than ever; swiftly adapting new technologies, tailoring their attacks using novel methods, sharing information or intelligence and cooperating closely with each other

3 new risk management strategy
1. Distributed, Immutable and Ephemeral (D.I.E) Traits
CIA may be able to help us detect, protect and respond but probably not able to address recover. The aim is not about stopping attacks but to make attacks irrelevant and hence more resilient We should design our systems to be resilient by designing for D.I.E before we address the C.I.A.
2. Security Chaos Engineering
In Security Chaos Engineering:
-
Security capabilities must be end-to-end instrumented.
-
Security must be continuously instrumented to build confidence in the system's ability to withstand malicious conditions.
-
Readiness of a system's security defenses must be proactively assessed to ensure they are battle-ready and operating as intended.
-
The security capability toolchain must be instrumented from end to end to drive new insights into not only the effectiveness of the functionality within the toolchain but also to discover where added value and improvement can be injected.
-
Practiced instrumentation seeks to identify, detect, and remediate failures in security controls.
-
The focus is on vulnerability and failure identification, not failure management.
-
The operational effectiveness of incident management is sharpened.
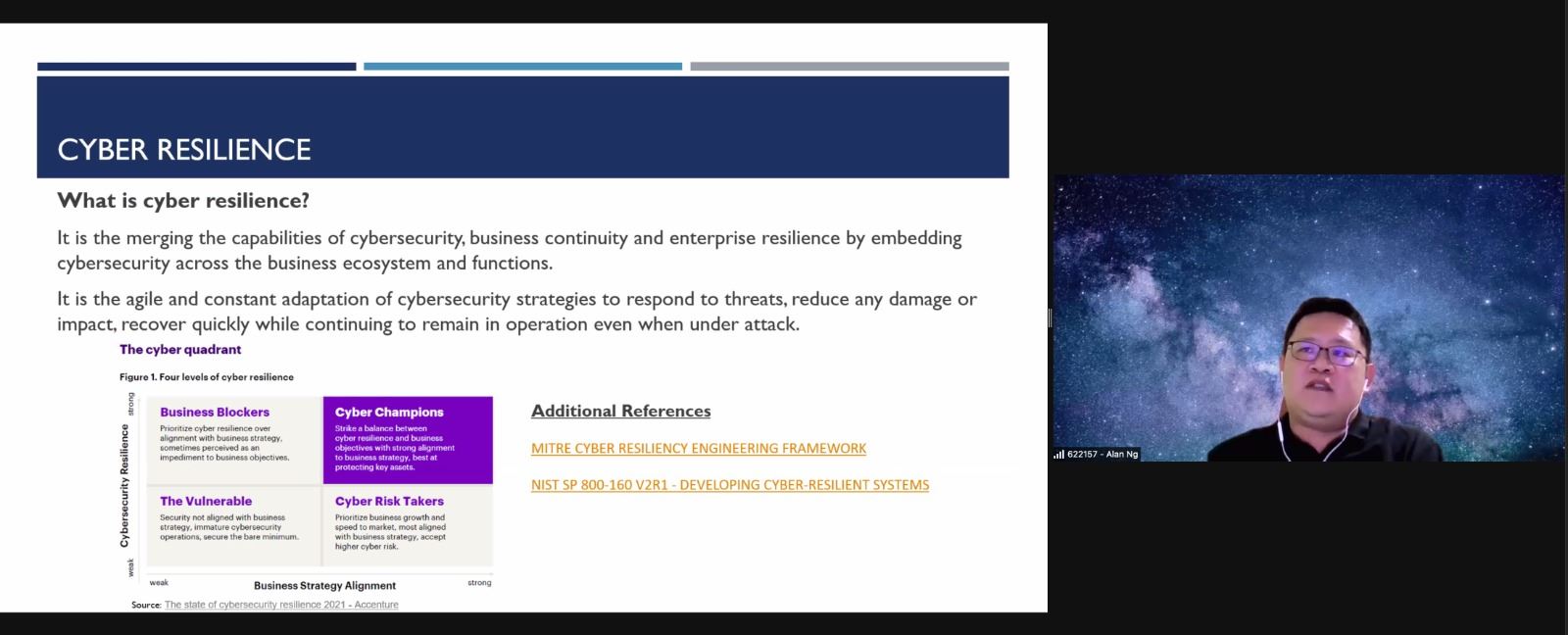
3. Zero Trust
6 areas or category of things to be included in the zero-trust strategy.
- Users - Knowing who/what is requesting access at what time is critical. Identity or users must be established, validated, authenticated and verified explicitly, not inferred from the environment.
- Data - Restricting data access, processing and flow. Protecting data at-rest and in-transit.
Networks - Mitigate lateral movement or unauthorized access by using an intelligent, adaptive segmentation strategy for workloads or network connection. monitoring for and protecting against anomalous traffic patterns or even behaviors.
- Applications - Lockdown application access and configuration must be secure to mitigate application risks.
- Infrastructure. Utilizing your cloud fabric according to best security principles, utilizing the intelligence and protection provided.
- Devices. data access requests result in the transfer of that data to a browser or app on a device. Knowing the state of that device is critical in a world where devices can be infected, lost, or stolen.
Through the survey feedback, many participants appreciate the practicality of use cases illustrated. I believed its a good learning lesson for me as it is for all of you.
Thank you to our guest speaker, Mr Alan Ng and fellow members for the participation. Join us for the next “Learning Never Stops” event brought to you by (ISC)² Singapore Chapter!
Webinar Topic :Examining the Anatomy of OT
Speaker: Matt Loong

We started our first event of the year 2022 addressing the topic of examining the anatomy of OT. The history of Operational Technology (OT) has actually been around for a very long time, for example with Archimedes' machines and Davinci’s invention. But it really took off with the industrial revolution in the 18th and early 19th centuries, with many factories adopting mechanization and mass production. In the 1970s, automation with computers and electronics started to permeate into processes, with the birth of the PLC as well. Today, we have a flurry of digitized technologies monitoring and controlling cyber physical systems along with internet of things. OT is prevalent in many aspects of our daily lives – from defence, industries, to urban living. There are 11 critical sectors designated in Singapore, many of them have OT; outside of the designated 11, there are even more OT in other potentially critical sectors e.g. oil and gas, waste management, food processing and manufacturing.
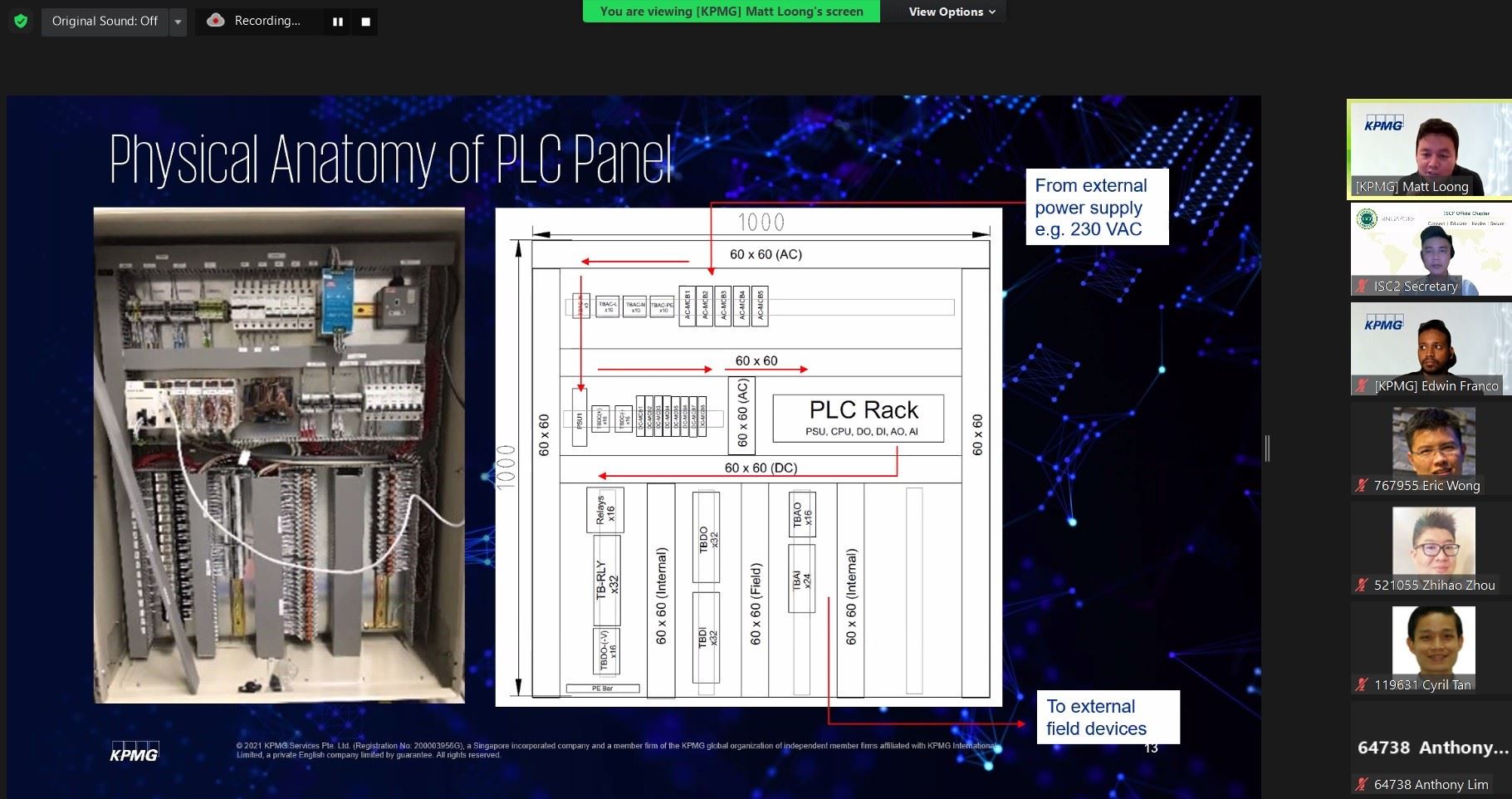
But what exactly are some examples of operational technology today? For example, Supervisory Control and Data Acquisition systems (SCADA) are typically applied to monitor and control geographically dispersed systems in remote locations. Distributed Control Systems (DCS) are systems with multiple controllers and integrated applications typically used within a single location, such as a manufacturing plant Programmable Logic Controllers (PLC) are single closed looped controllers within a localised plant. Examining OT from the field to control room, on the plant floor we have the field process area with valves, pumps etc. They are wired via cables to marshalling junctions boxes and finally to the PLC panel. Downstream of the PLC panel is the control room with various human machine interfaces. A common model adopted in OT is the Purdue Model where there is Level 0 Process, Level 1 Basic Control, Level 2 Area Supervisory Control, Level 3 Site Manufacturing Operations and Control, and Level 4 Enterprise Zone.

There are 4 main PLC programming paradigms – ladder, function block, structure text and instruction list. In addition to programming paradigms, there are various protocols used in OT. Protocols are standards for exchanging data. They are not programming languages. There are many OT protocols. Some are open source while some are proprietary to the vendor. They include examples like Modbus, DNP3, BACNET etc. In recent times, there have been many cyber-attacks on OT systems. Hence the importance of Network Security Monitoring, including North South traffic across network perimeter, as well as East West traffic between hosts. Graceful degradation is also important, availability of service must be safely ensured despite failure by cyber-attack; this thwarts the fundamental purpose of the Threat Actor’s effort.
The future of OT promises great potential in the advancing technologies of 5G, machine learning, edge computing, and blockchain.
During the webinar, there were many interactions between the participants and speaker, most would have gotten a couple of takeaways from the sharing to improve on their own cybersecurity posture.Thank you all for participating. Join us at our next LearningNeverStops event.
- Home
- Events
- Upcoming and Past Events
- Events Coverage 2022
