Secure Singapore 2021: 6 Nov 2021:
We were very honored to have Mr. David Koh, Chief Executive of Cyber Security Agency of Singapore grace our event as the Guest-of-Honour to deliver the opening address.
We were also very honored to have Ms. Clar Rosso, CEO, (ISC)2 from USA address the 180+ attendees with her insightful welcome address. "Singapore Cybersecurity Strategy 2021" was presented by Mr. Yik Jia Wei, Director - Strategy & Planning from CSA.
This was followed by an exciting series of keynote sessions on a variety of topics well aligned to our theme for the 2021 Annual Singapore chapter conference: " Rising Above and Staying Resilient Against Future Threats"
We greatly appreciate our esteemed speakers who volunteered to share their knowledge with the community, and also to our sponsors, who were instrumental in making this event possible.
The sessions were all power packed with great content and insightful, relevant and current cybersecurity topics that ranged from the importance of AI, strategies for cyber insurance, regulatory trends in AI adoption, supply chain risk management, resilience from Ransomware attacks, Cloud native security and influencing human behavior in reducing cyber risks.
The Panel discussion towards the end was very refreshing as well where four speakers from different industries shared their views and opinions on risks related to Emerging technologies and provided safe adoption measures for AI, Blockchain, IoT, OT and 5G technologies.
The event ended with a fun Kahoot quiz, sponsored by Aqua Security and the entire program was very well received by the enthusiastic attendees - our (ISC)2 Singapore Chapter members. Each session also had interesting Q&As as well from the attendees and the event started and ended as per the exact planned timings.
We thank our (ISC)2 Singapore Chapter EXCO and Sub-committee members who planned and ensured a smooth execution of the entire event and our chapter President Mr Garion Kong for his support and guidance all through and our chapter advisor and immediate past president, Mr Victor Yeo for his support as well.
(ISC)2 Singapore Chapter Learning Never Stops Virtual Sharing #09 on 13th Oct 2021:
Webinar Topic: Least Privilege in Public Cloud environments
Speaker: Mr. Rajnish Garg, Solutions Engineer (ASEAN), CyberarkLeast Privilege is one of the most interesting topics where many Government, Enterprise and Cybersecurity Community are concerned with. Today, we are very fortunate and honored to have Mr. Rajnish Garg, CISSP taking precious time off from his busy schedule to share with us on how to achieve least privilege in AWS and Azure.
The webinar begins with sharing around the Capital One breach and how millions of records were stolen due to excessive permissions assigned on their EC2 instance. Then we learned briefly at the latest vulnerability on Microsoft Azure named Azurescape that can easily lead attackers to gain access to the containers of customers running their application using Azure Container Instances service.
After that speaker did share the types of identity and permission model of AWS and Azure. And how both public cloud providers have different way of configuring the permissions and why understanding what all permissions is really required by each cloud entity is almost impossible task.
Finally, he concluded his presentation and demo with sharing around Cloud Infrastructure Entitlement Management (CIEM) domain and how such solutions can easily address the challenge on achieving the least privilege across multi-cloud or any single cloud environment.
Congratulations to all the 3 x Quiz Kahoot Winners and they did receive the Laptop stand from our Speaker.
Through the survey feedback, many participants appreciated the fact that examples were shared throughout the sessions along with demonstration on how AWS Policy and Azure roles are being configured.
Thank you to our guest speaker, Rajnish Garg and fellow members for the participation. Join us for the next “Learning Never Stops” event brought to you by (ISC)² Singapore Chapter!
(ISC)2 Singapore LearningNeverStops Virtual Sharing #08 on 30 September 2021:
Webinar Topic: The Key to Secure Digital Transformation is SASE + Zero Trust
Speaker: Mr. Jonathan Andresen, Senior Director Marketing & Products (APJ), Bitglass

On September 30th, 2021, (ISC)2 Singapore Chapter has warmly welcomed the our sponsored speaker Mr. Jonathan Andresen, Senior Director Marketing & Products (APJ) at Bitglass to provide us insights on the key journey to a secure digital transformation.
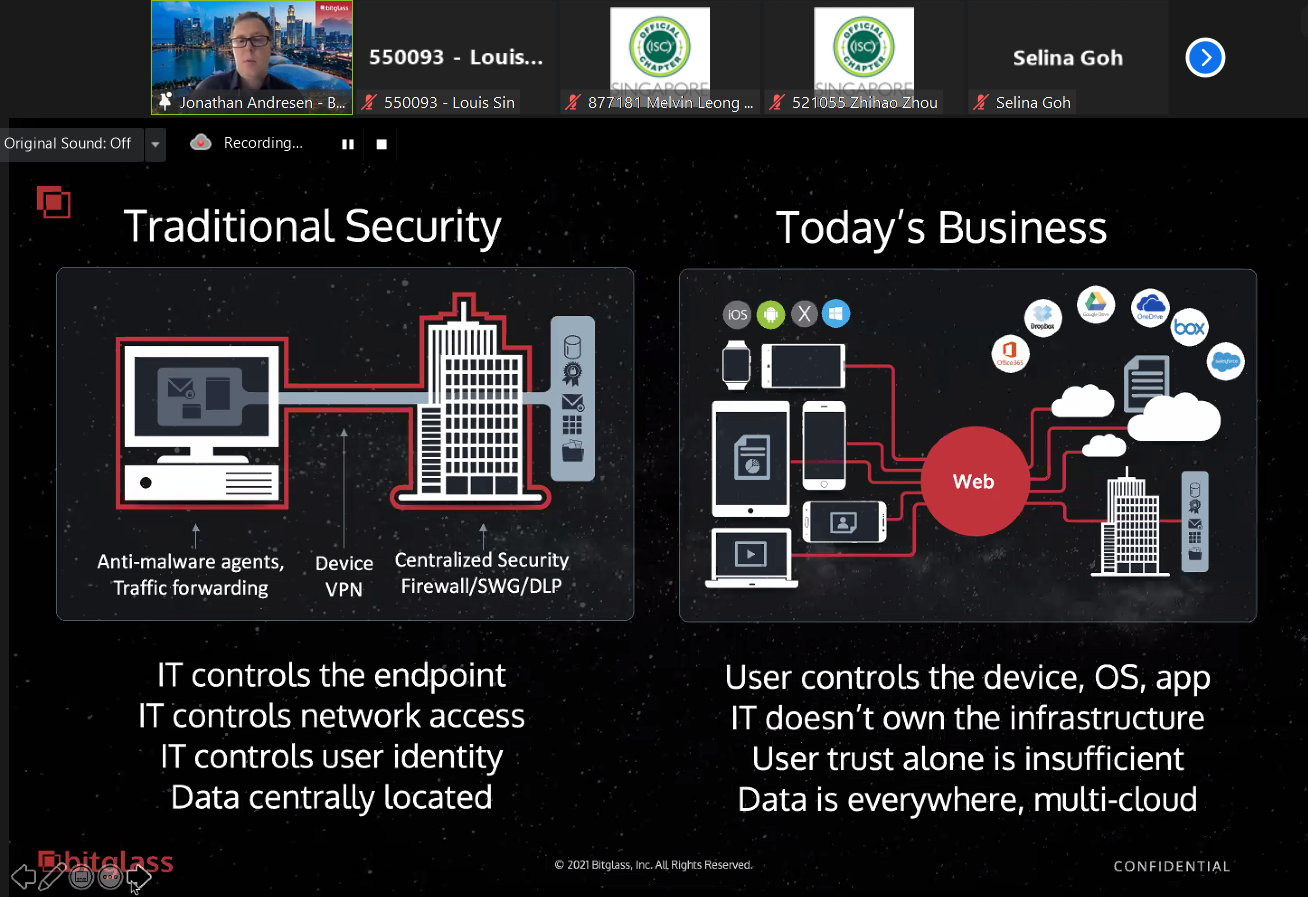
Network security architectural best practices are undergoing a dramatic shift. Two key terms have come to dominate infosec discussions among IT professionals: Zero Trust Network Access (ZTNA) and Secure Access Service Edge (SASE). In practical terms, which is more important, what is the relationship between them, and how will they improve cybersecurity effectiveness?
As security teams in Singapore and around Asia prepare for either a return to the office or a more distributed workforce, and as cyber threats continue to proliferate, it’s essential for security leaders to understand the practical differences between these two security paradigms, and how to implement them effectively. This presentation cuts through the hype to explain the fundamentals of SASE, Zero Trust, and how they are fundamental pillars of modern enterprise security.
The essential elements and major differences between Zero Trust and SASE; Seven critical SASE & Zero Trust use cases that you can leverage;
How SASE simplifies security operations, lowers management overhead and improves ROI; and Practical steps to implementing Zero Trust and SASE security.
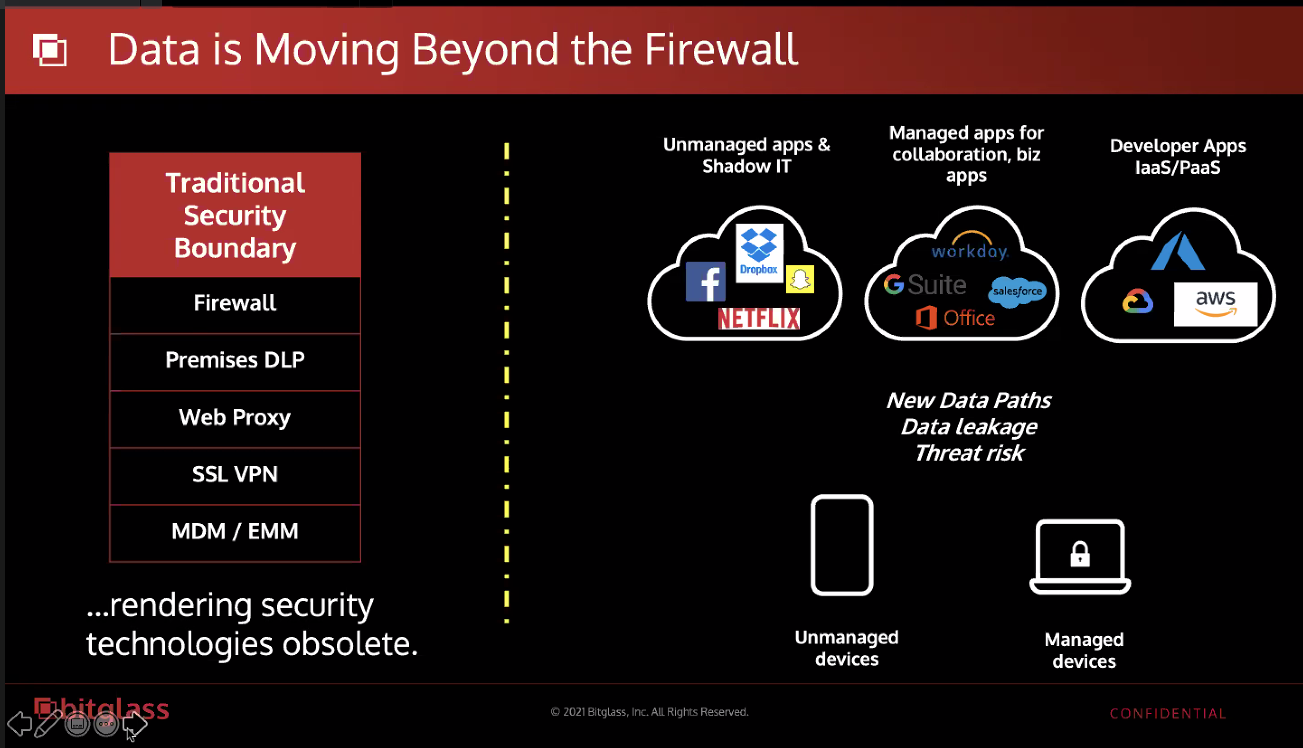
On top of that, Mr Jonathan also underline the importance of integrating CASB and Secure Web Gateway as essential elements of your organisation cybersecurity defense to protect data in the cloud as well as embracing remote working.
There were many interaction between the audiences and the speaker in fact, we running out of time to address all the queries!
Before we wrapped up our session, the audience were treated to a fun and entertaining Kahoot Quiz Challenge. Congratulations to all quiz winners! Bitglass is one of the most generous sponsors to date as the prizes ranges from $60 to $200!
For those who like to have a copy of the presentation slides, it can be found on the (ISC)2 member portal.Once again, thank you to our sponsor, Bitglass, speaker, Mr. Jonathan and fellow members for the participation. Join us for the next “Learning Never Stops” event brought to you by (ISC)² Singapore Chapter!
(ISC)2 Singapore LearningNeverStops Virtual Sharing #07 on 9 September 2021:
Webinar Topic: Container Orchestration is here, what does it mean for security?
Speaker: Mr. Tan Zhihao, Director, Solution Architects - APJ, Aqua Security
Container security is one of emerging areas where many IT or even cybersecurity professional is very concerned with. Today, we are very fortunate and honored to have Mr. Tan Zhihao, Director, Solution Architects -APJ of Aqua Security taking precious time off from his busy schedule to share with us his area of expertise.
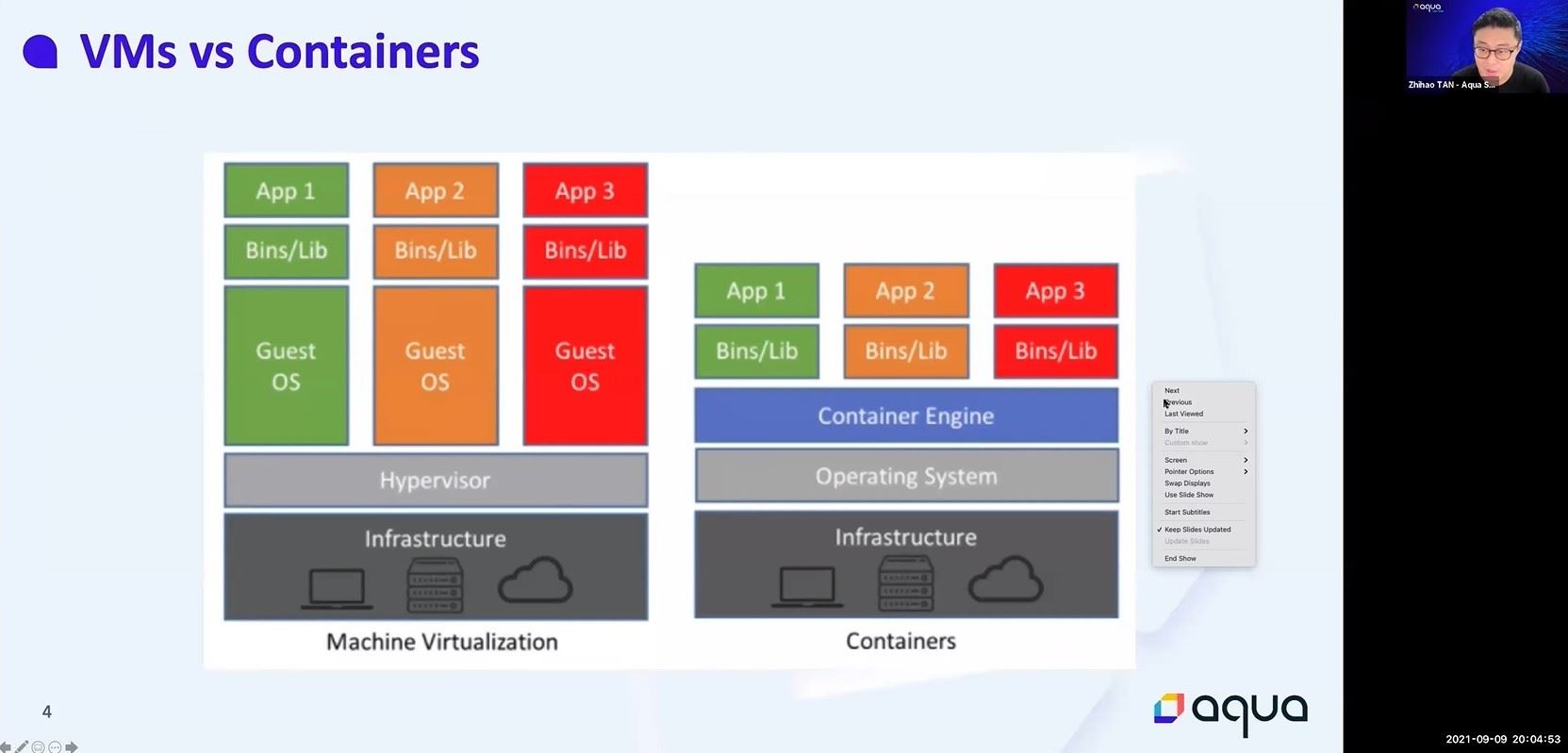
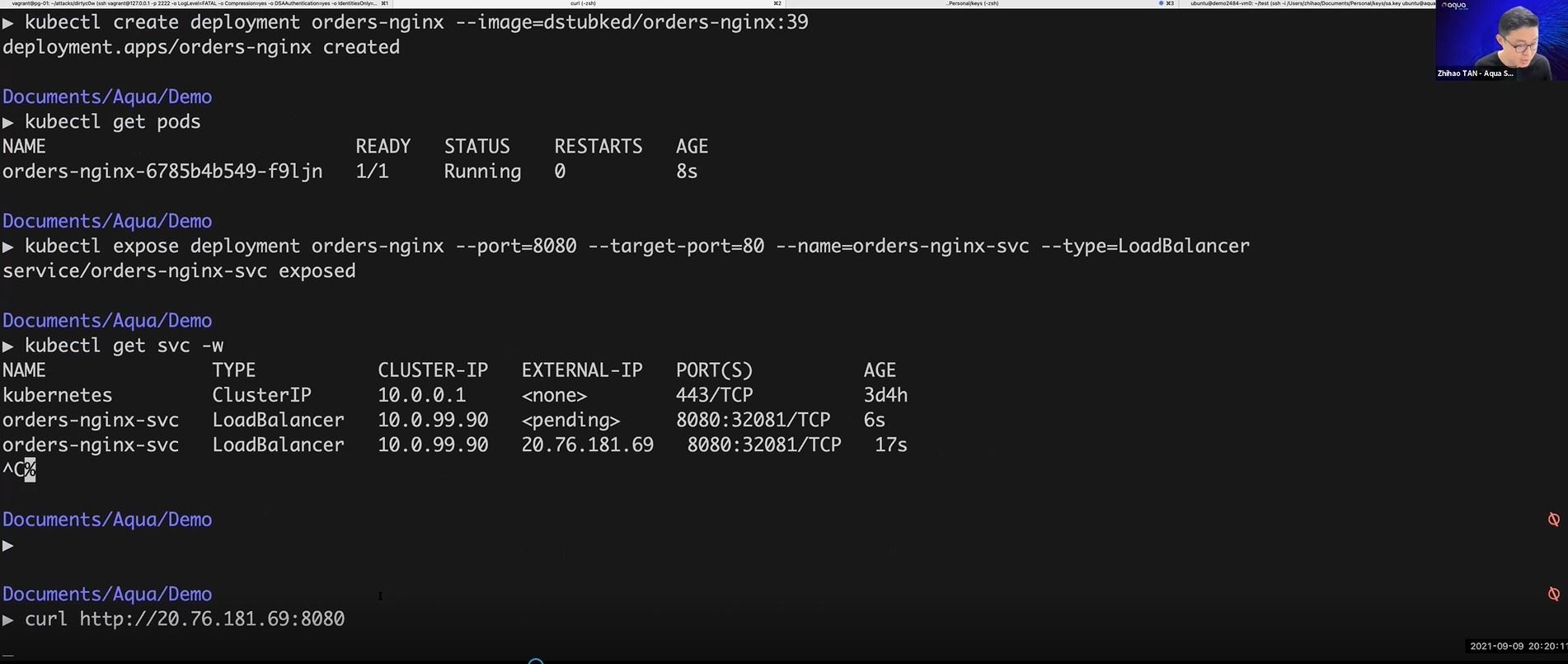
With containers and container orchestration technologies like Docker and Kubernetes gaining mainstream enterprise usage and facilitating the usage of cloud native applications, there can be a lot of buzzwords that is obscuring what is going on from a security standpoint.
When we look at the security posture of a cloud native environment, there are 3 major areas that impacts the overall security posture of an environment. These 3 areas are artefacts developers build, infrastructure that runs the containerized workloads and the actual running workloads themselves.
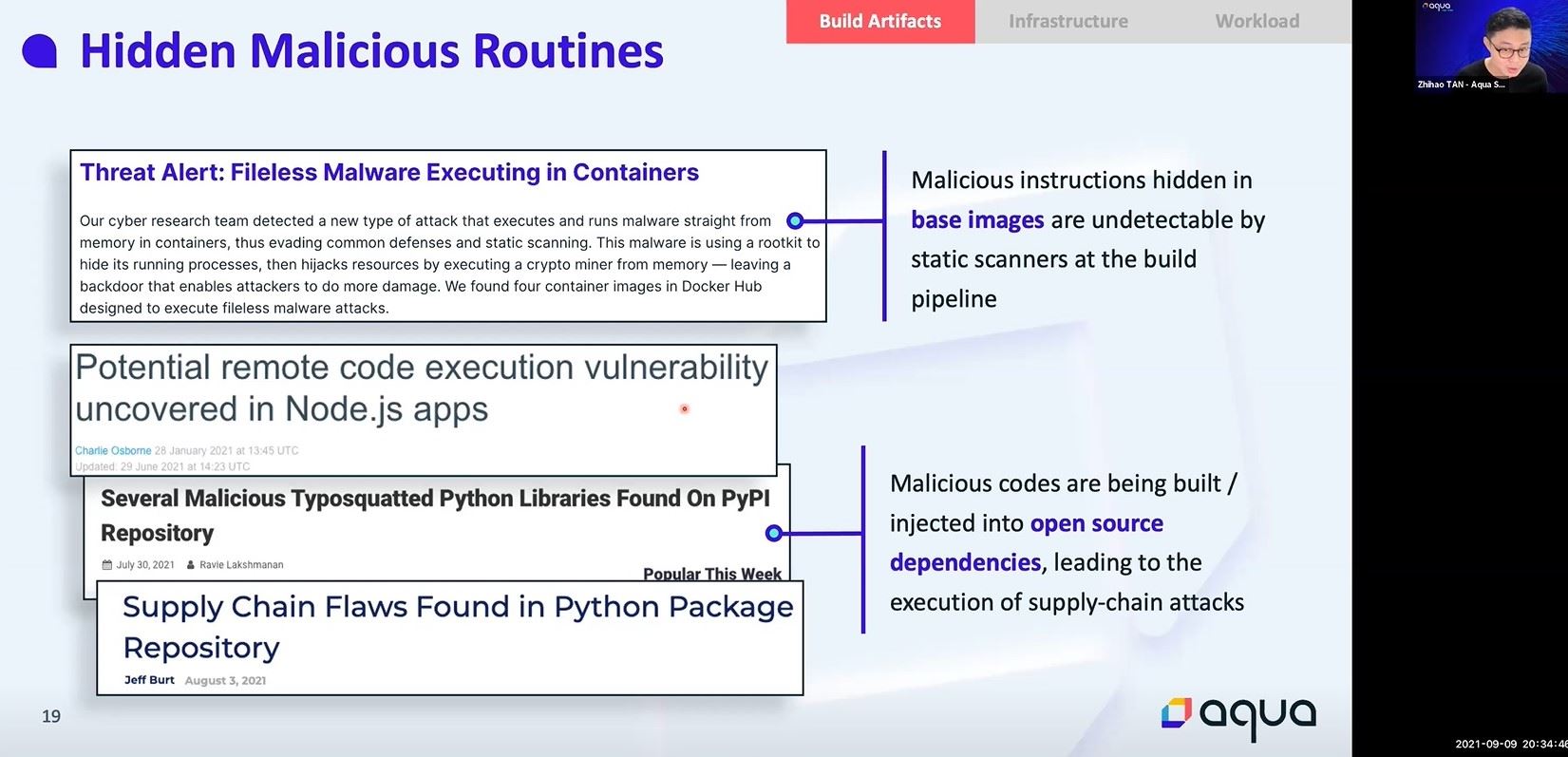
In this session, the attendees learnt that threats can exist within artefacts that the developers are building, where container base images or opensource programming libraries originating from the Internet can contain malicious code which are hidden from the view of traditional security scanners thereby introduced into a victim’s environment through supply chain risks.
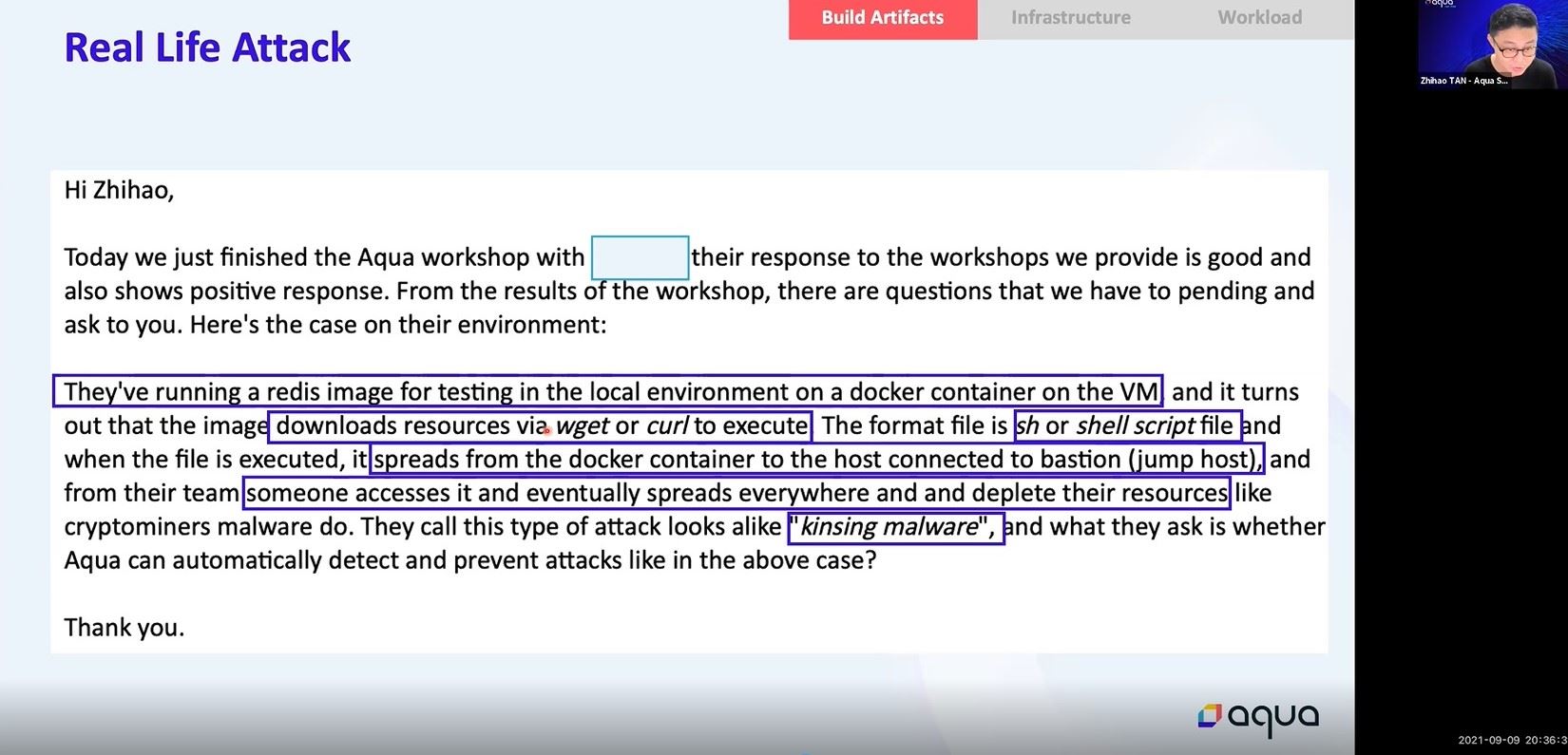
Artefacts can also be deployed on top of infrastructure that are prone to misconfiguration allowing cluster takeover by a threat actor. Last but not least, running containerized workloads can also be exploited by attackers in order to elevate their privileges in order to gain a foothold in any given environment.
This is one of the rare webinars that we have a guest speaker presenting as well as performing live stream hands-on demonstration.
The attendees also learnt how they can leverage cloud native security concepts such as shifting security left through a combination of both static analysis and sandboxing of artefacts introduced through the supply chain as well as leveraging cloud native characteristics such as workload immutability in order to protect their environment from a new generation of threats.
Kudos to Mr. Tan, through the survey feedback, many participants appreciate the effort, knowledge and thoroughness on the coverage preparation. Once again, thank you to our renowned guest speaker and fellow members for the participation. Join us for the next “Learning Never Stops” event brought to you by (ISC)² Singapore Chapter!
(ISC)2 Singapore LearningNeverStops Virtual Sharing #06 on 16 August 2021:
Webinar Topic: The Next Generation DLP. Know More, Risk Less.
Speaker: Dr. Alexey Raevsky, MBA, Co-Founder and CEO at Zecurion.

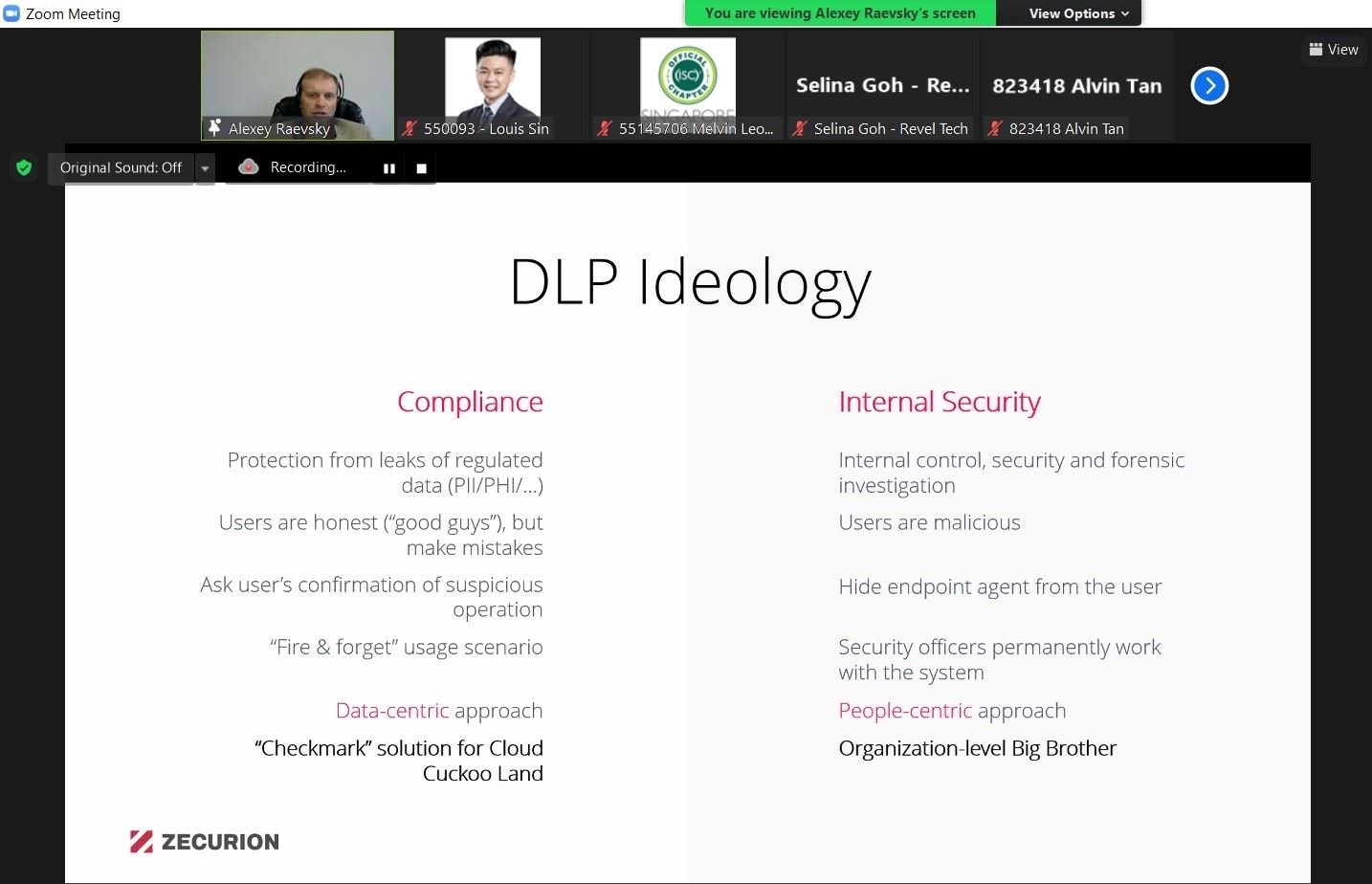
On August 16th, 2021, (ISC)2 Singapore Chapter has warmly welcomed the new speaker Dr. Alexey Raevsky, MBA, Co-Founder and CEO at Zecurion. Mr.Raevsky has introduced the Next Generation DLP concept and explained the difference to the classic ones, basing on Zecurion innovations.
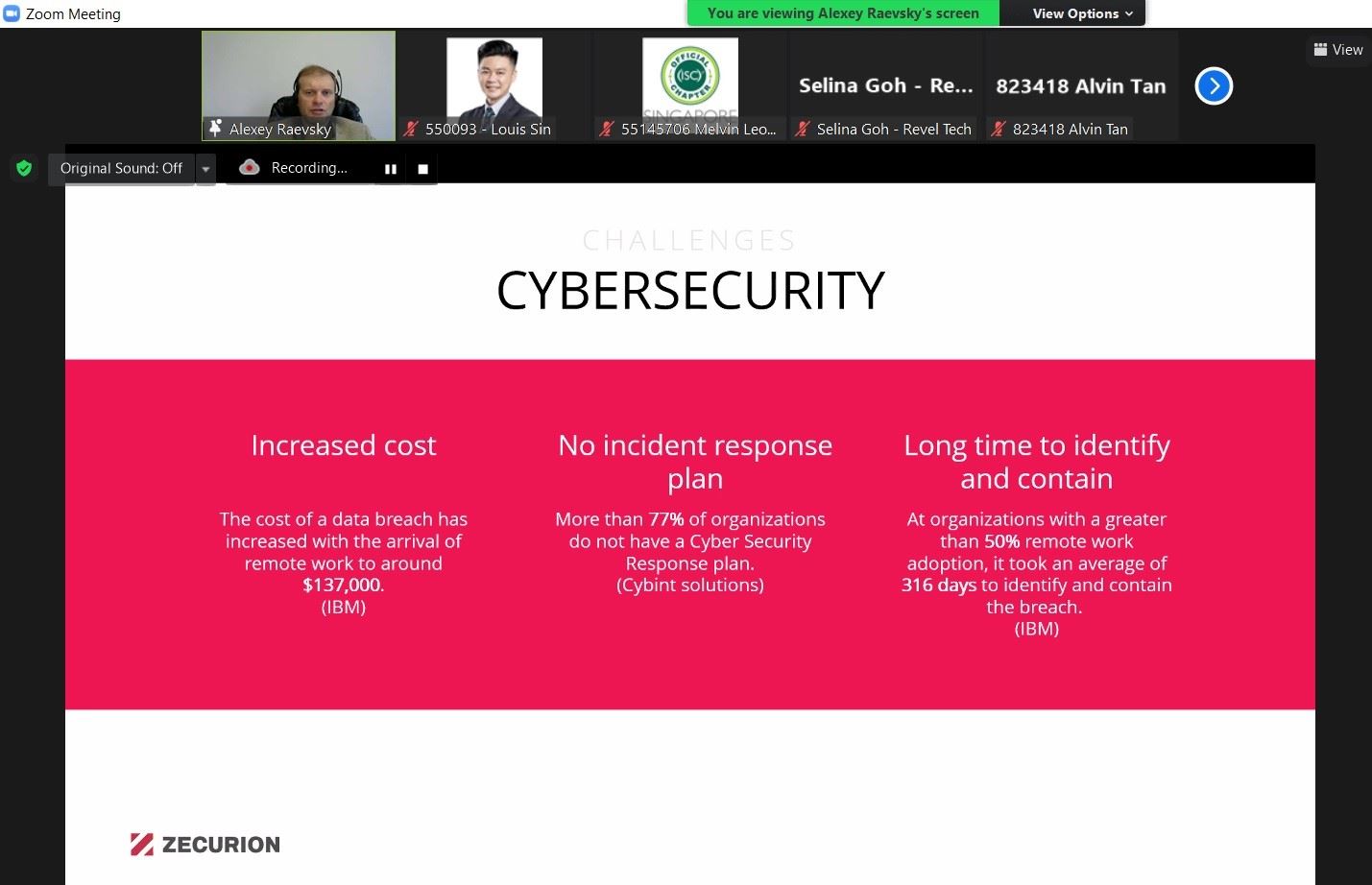
The Next Generation DLP introduces the new level of effective detection of internal fraud and risk-based data loss prevention in the context of massive remote work.
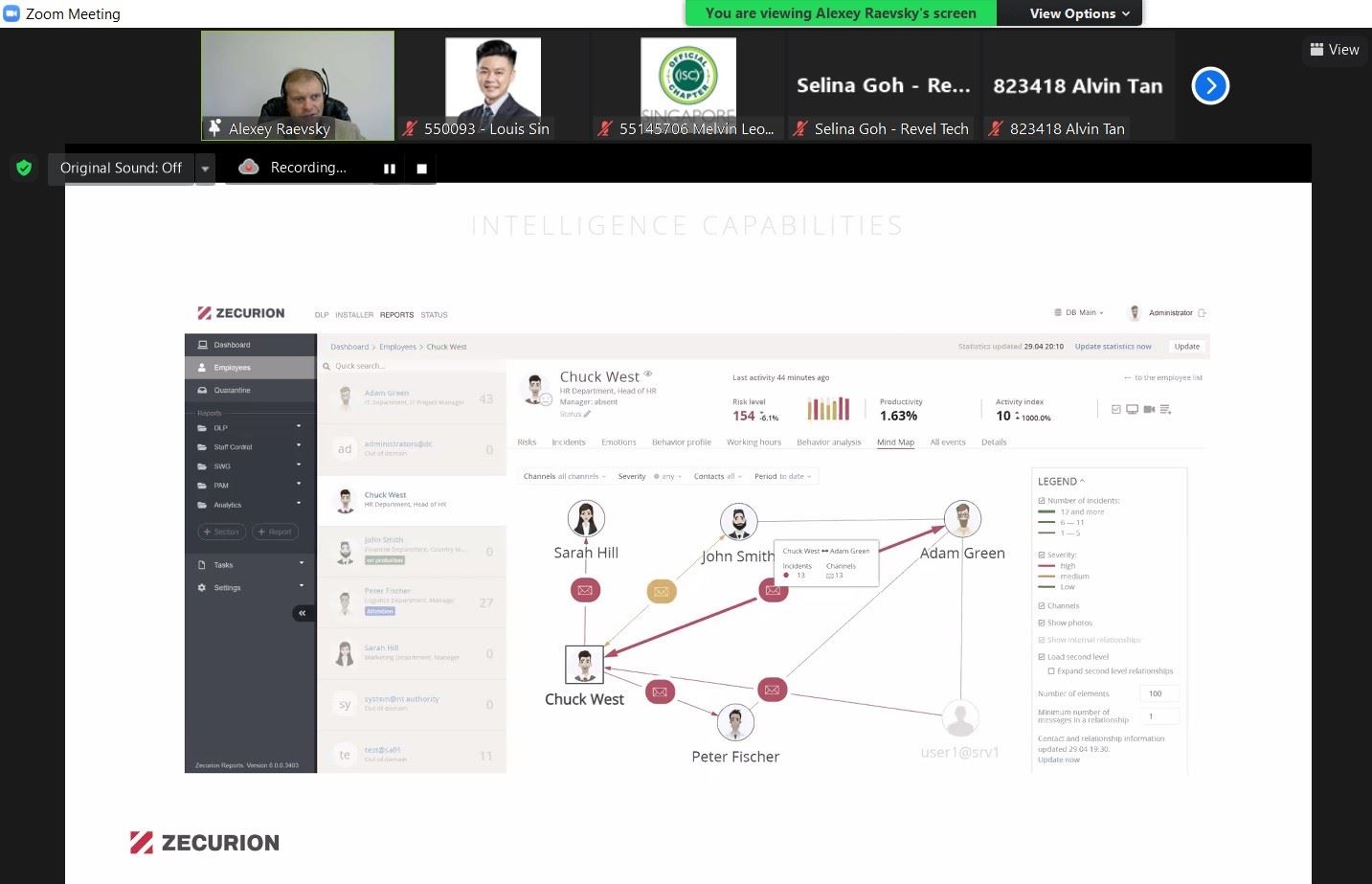
Traditional systems protect communication channels and devices, preventing sensitive data from being sent outside the network perimeter. The Next Generation DLP can do both and on top of that has advanced control, analytic, and intelligence capabilities to identify whether user behavior is abnormal and pose a risk for the company.
The use of this solution essentially improves the internal security posture of an organization comparing to the classic DLP.
Congratulations to all the 5 x Kahoot! quiz winners as Zecurion decided to increase the number of prizes from 3 to 5! Over here, we would like to thank our sponsor, Zecurion, guest speakers; Dr. Alexey and fellow members for the participation.

According to the event feedback, the audience found the webinar very helpful. The event was rated as “very good” and excellent”.
Dr. Alexey Raevsky’s presentation slides can be found on the (ISC)2 member portal. Do join us for the next “Learning Never Stops” event brought to you by (ISC)² Singapore Chapter!
(ISC)2 Singapore LearningNeverStops Virtual Sharing #06 on 14 July 2021:
Webinar Topic: Infrastructure is the New Code – Is Your DevSecOps Ready?
Speaker: Mr. Ori Bendet, Mr. Edwin Lee
We welcome back one of our returning speakers, Mr Edwin Lee who has just joined Checkmarx as ASEAN director, provide us a brief overview on his company's profile, customer base as well as highlighting the importance of 35% of the breaches are attributed to web applications. With the ever increasing of SaaS security solutions and BYOD trend adopted by organizations, it's imperative that application security has a role to play as part of the cybersecurity eco-system.
Mr. Ori Bendet, Director of Product Management set the stage by introducing the agenda to provide a glimpse of what are the key takeways for today's webinar:
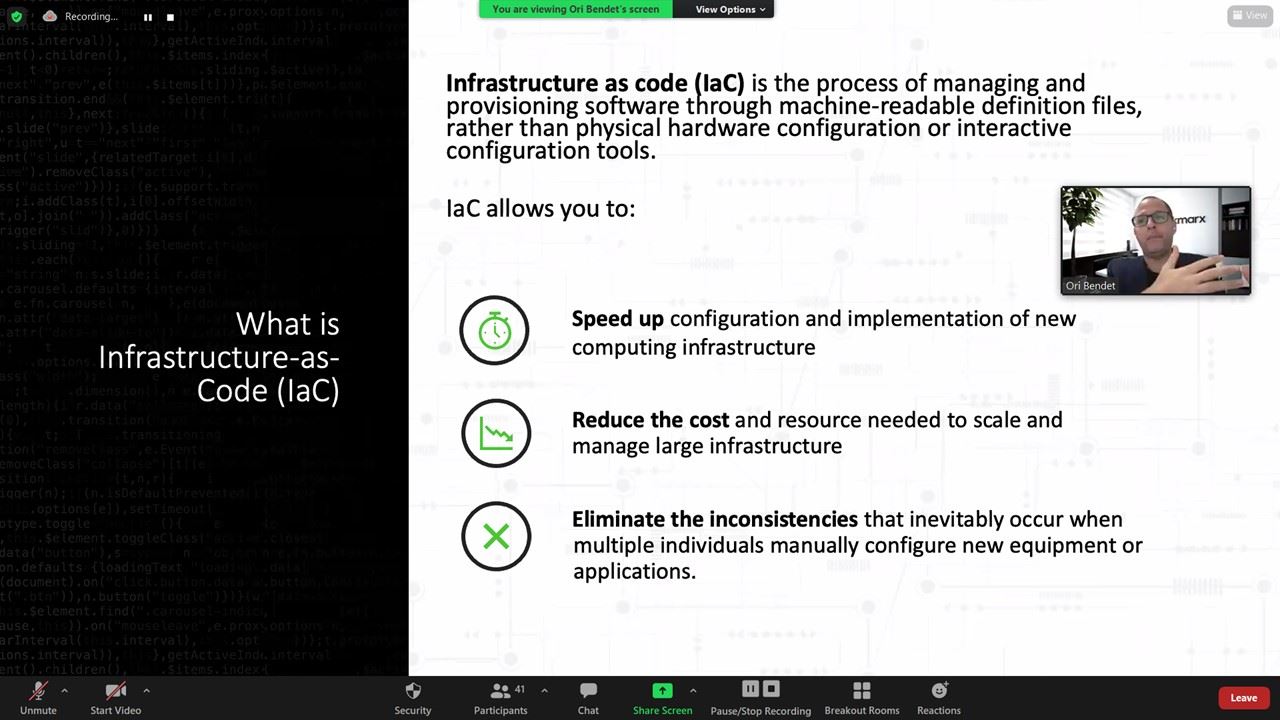
- What is Infrastructure-as-code (IaC)?
- What is KICS ?
- Live Demo
- KICS 2021 Roadmap
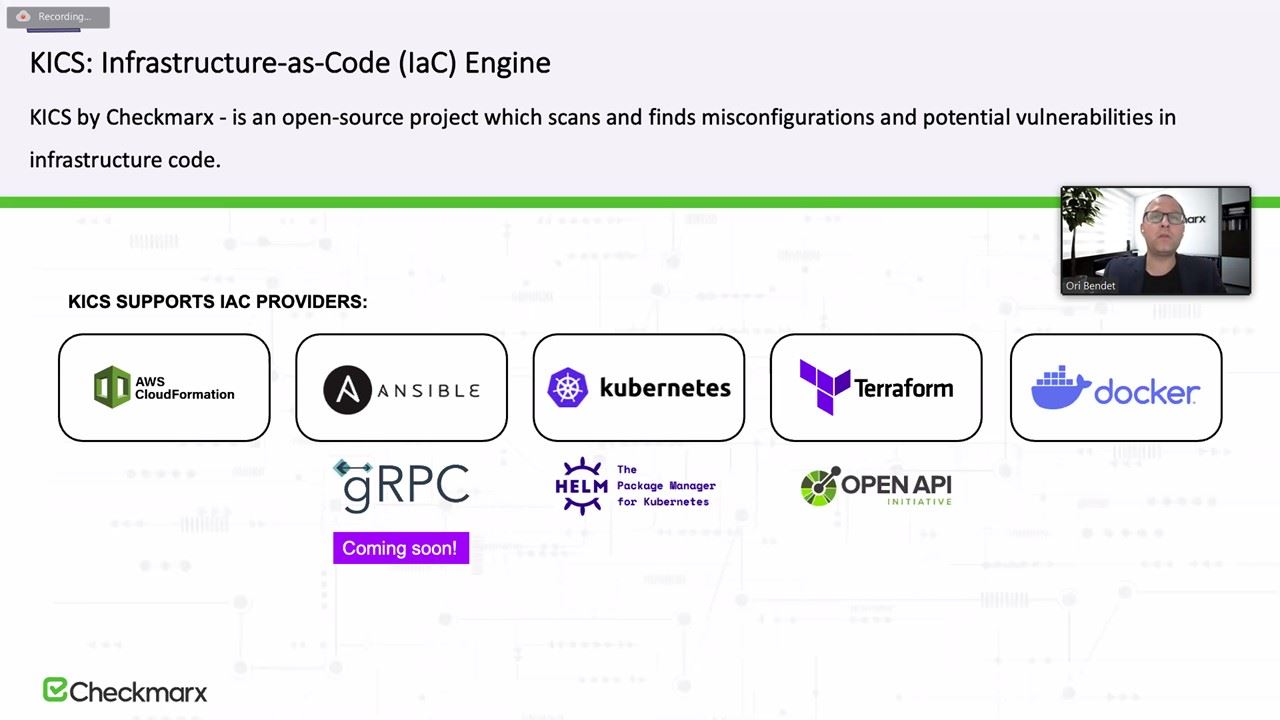
With the raise of cloud native technologies and the speed of DevOps, we now have new technologies to support the cloud-native infrastructure. Infrastructure-as-Code (IaC) is one of those technologies. IaC allows you to manage your infrastructure as code and manage it at the speed of DevOps. However, IaC security is a concern and can possess a real risk to your system. In this session, we discussed what are the security risks of IaC and how you can mitigate those risks using KICS, an open source project which scans and finds misconfigurations and security issues in your infrastructure code.
During the Q&A sessions, there were some interesting exchanges between attendees and Mr. Ori.
Mr Ori responded with ease and shared his experiences and point of views on how Checkmarx is able to handle such challenges.
Before we wrapped up our session, the audience were treated to a fun and entertaining Kahoot Quiz Challenge. Congratulations to all quiz winners!
We would like to thank our sponsor, Checkmarx, guest speakers; Mr. Ori Bendet & Mr. Edwin Lee and fellow members for the participation. Do join us for the next “Learning Never Stops” event brought to you by (ISC)² Singapore Chapter!
(ISC)2 Singapore LearningNeverStops Virtual Sharing #05 on 17 June 2021:
Webinar Topic: Algorithmic Weaknesses - Is the Cybersecurity workforce ready for the future
Speaker: Mr. Gerry Chng
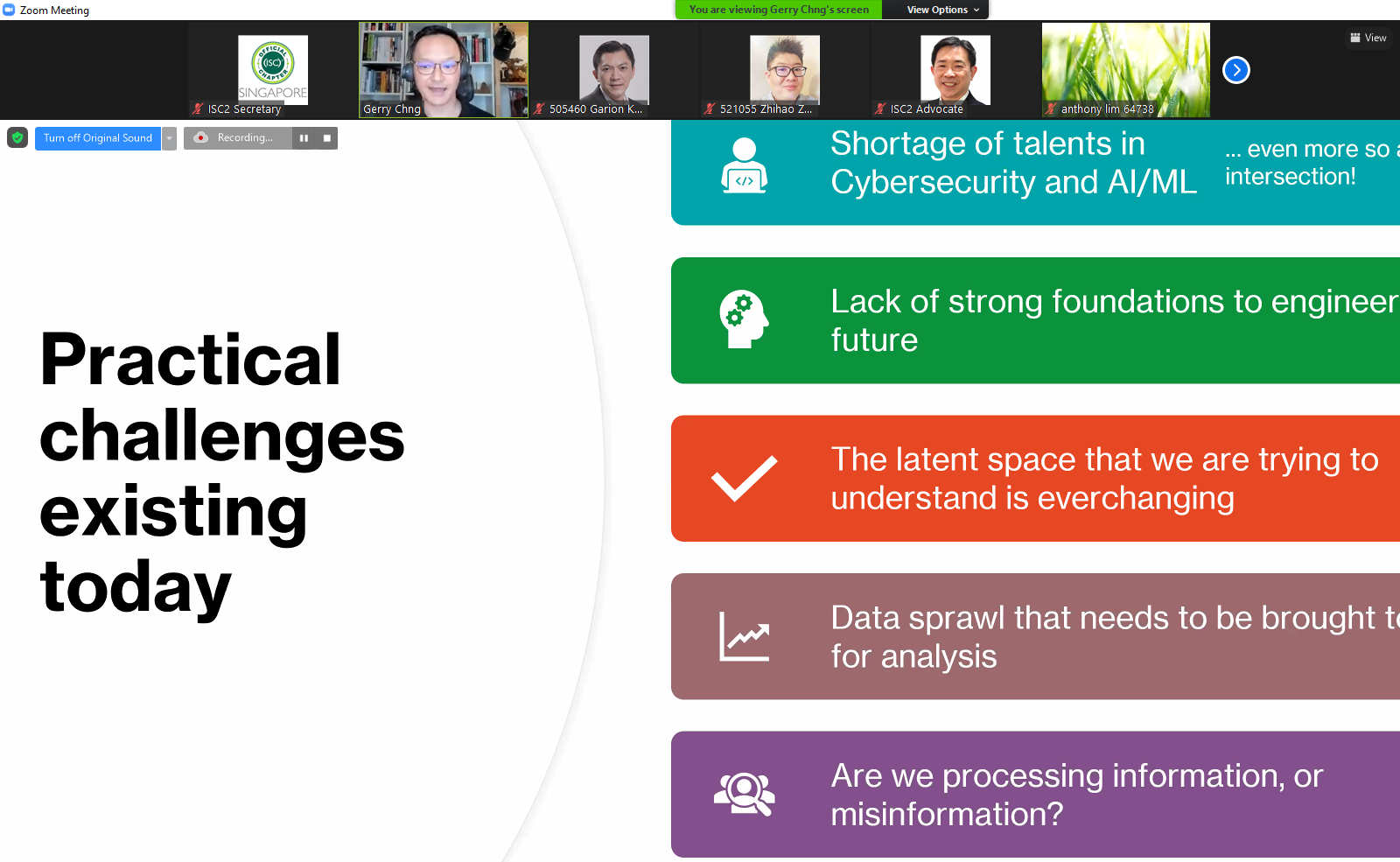
We are delighted to able to invite one of the most renowned speakers in the industry and always able to simplify complicated topic for audience to understand.
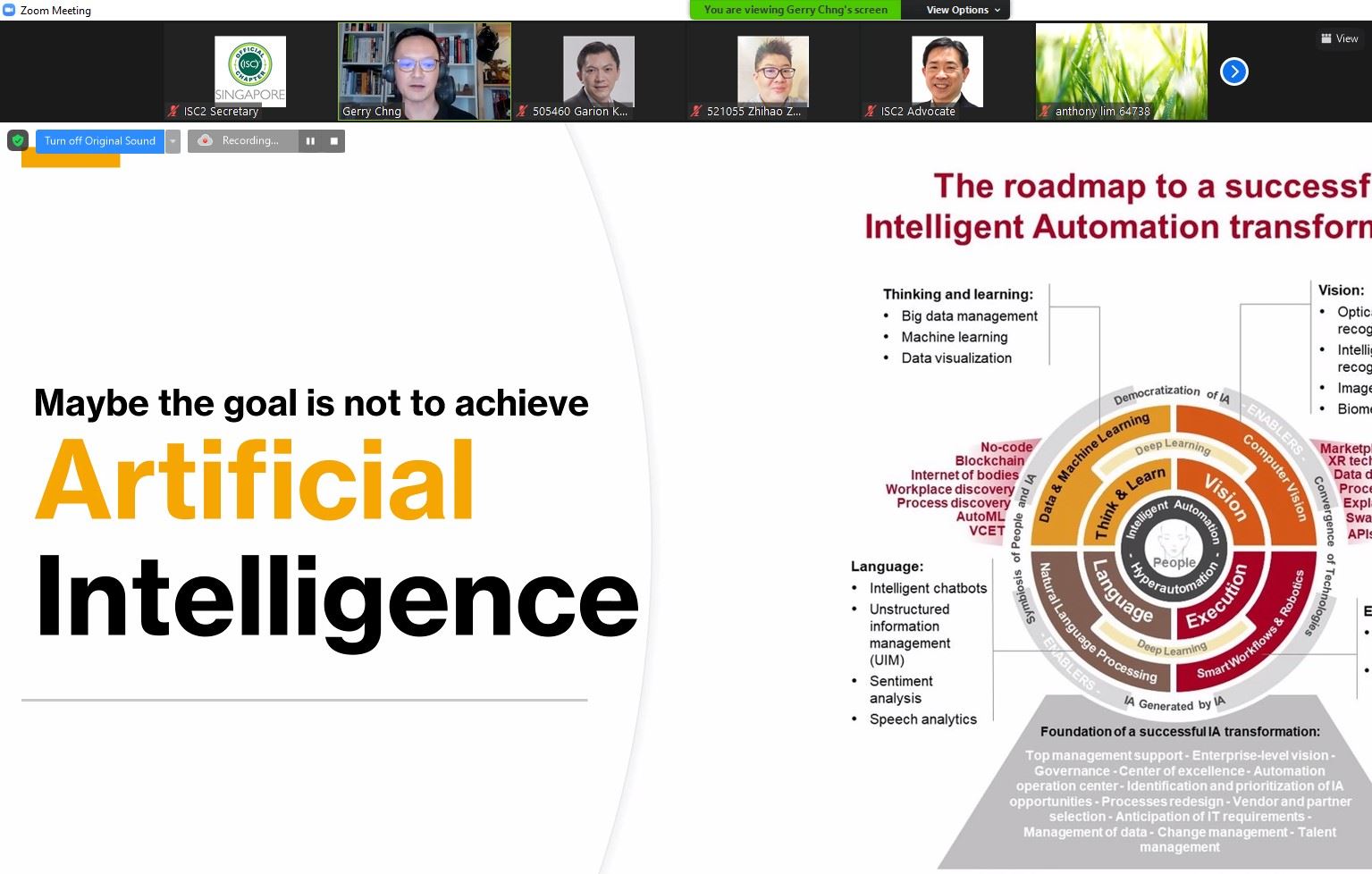
The increased interest and adoption of Artificial Intelligence has been made possible by the perfect combination of a few important factors. Ubiquitous access to mobile devices in most developed countries, increasing compute capabilities, improved algorithms, and the ever-growing base of data has all played an important role.
The promise of such emerging technology is undoubtedly exciting, and the webinar began by highlight some of the innovative solutions deployed to solve today's challenges. As with any technology systems, we need to ensure that these are designed, built, deployed, and operated with digital trust in mind.
However, some key differences between the deterministic nature of software as we are used to, versus the probabilistic nature of AI algorithms poses challenges in simply adapting tried and tested methods to test and secure today's AI systems. In fact, there are more known issues that actual technical solutions that could solve some of these adversarial attacks on the platforms.
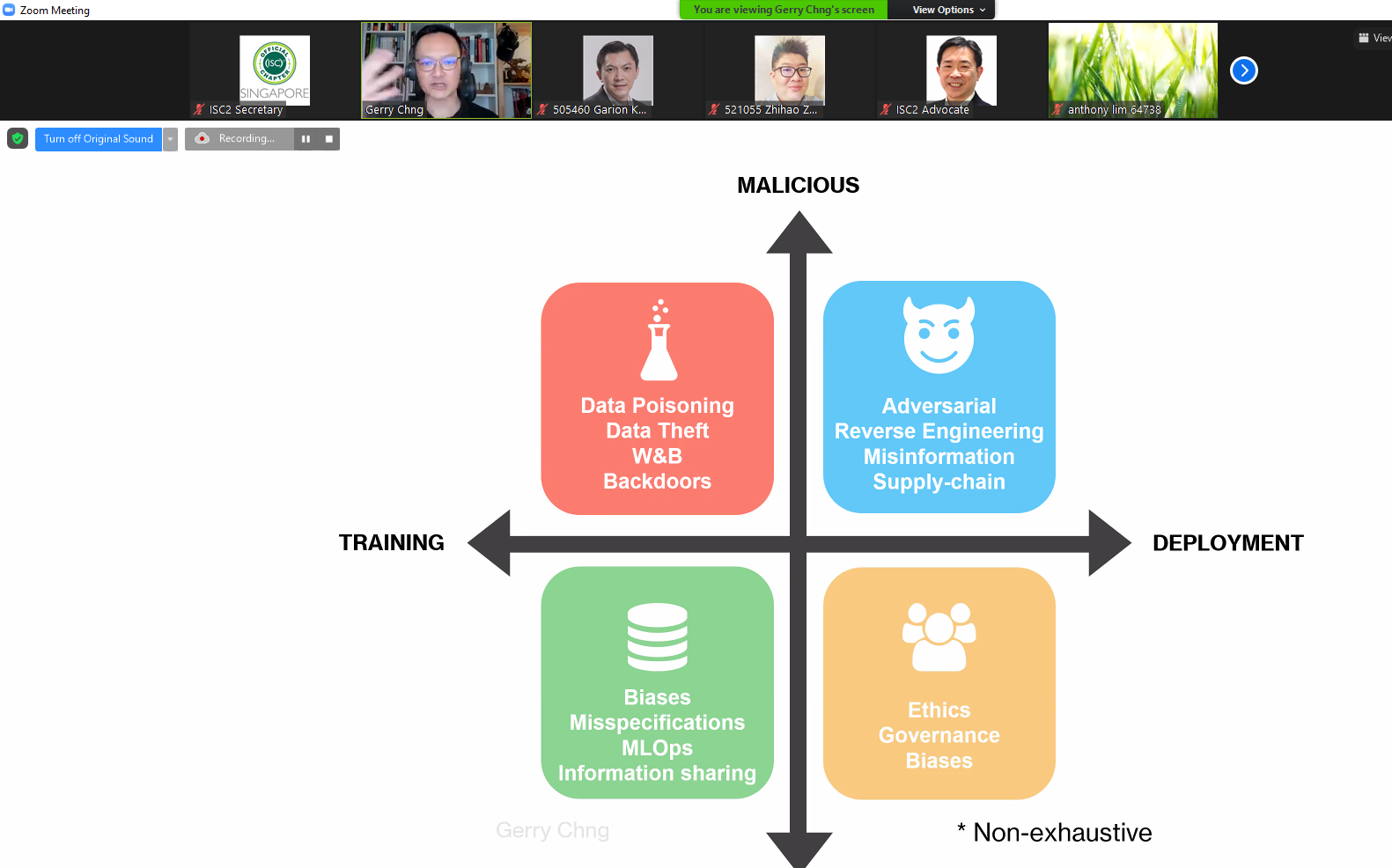
This talk then went on to provide several frames of references to categories attacks on AI systems. Two methods were discussed where they adopted a typical Machine Learning workflow to identify the attack surface area exposed.
But it is not just about the Cybersecurity aspects of AI.
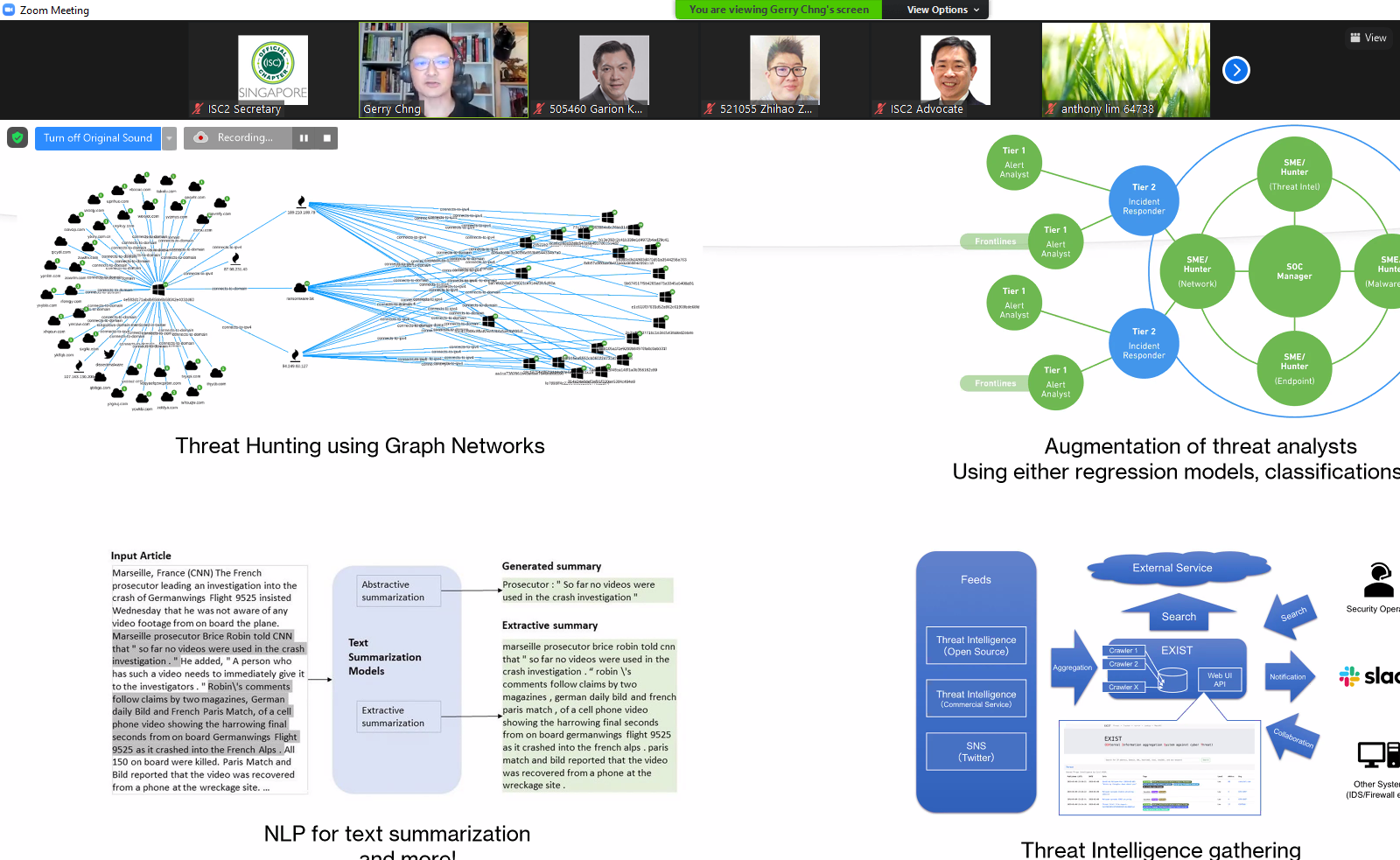
Such technology can also be used by hackers as offensive capabilities, or by Cybersecurity professionals to augment their ability to detect and respond to such threats. A few possible use cases involving graph network analysis for anomaly detection and containment was discussed, along with the use of language models to aid in the consumption of OSINT information.
The talk concluded by highlighting a few key areas in which Cybersecurity professionals should adapt their skills to be future-ready.
01 - Cognitive Skills
02 - Diversity
03 - Technical Capabilities
04 - Data Proficiency
05 - System Thinking
06 - Community Building
The future holds a great promise - provided we engineer it right with trust and respect for humans at the center.
Through the survey feedback, many participants has expressed their appreciation to Mr. Gerry & wish he could be invited back to provide a more in-depth session especially for AI for Cybersecurity used cases.
Thank you to our guest speaker and fellow members for the participation. Join us for the next “Learning Never Stops” event brought to you by (ISC)² Singapore Chapter!
(ISC)2 Singapore Chapter LearningNeverStops Virtual Sharing #04 on 18 May 2021:
Webinar Topic: Creating value from data—secure, and PDPA-compliant
Speaker: Dr. Maximilian Tschochohei
Despite few days into Phase 2 (Heightened Alert), it has not deprived us from continuous learning. The webinar begins by Dr. Max giving us a German lesson on how to pronounce his last name as per requested by audience. This also led to our topic of the day where many didnt realise how valuable & important data is. As data volume explodes & numbers of use cases grow, many businesses have capitalized on the opportunity and reaped benefits by improving efficiency, enabling new services as well as creating new business models.
However, there are always 2 sides of the coin - data can unlock big benefits but carries big risk too. Dr Max asked "What do we learn from these data breaches?" is Tech and business out of sync? do we collect and store data we do not need? Has data privacy become an after-thought?
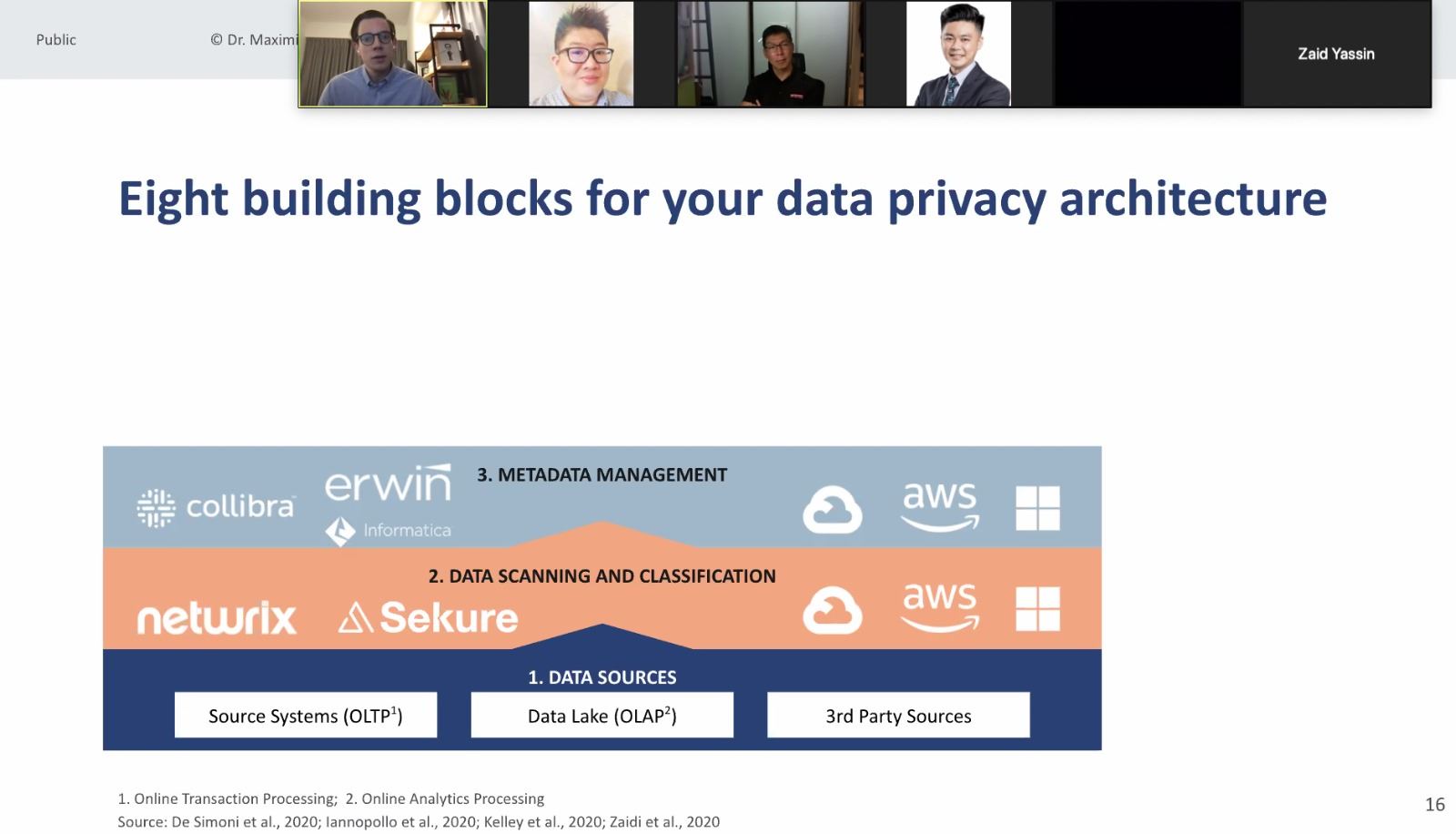
Data leaks are a real and significant threat and can often irreparably damage a business. To safely and effectively utilize data, organizations need to implement a data operating model. That would mean establish roles and responsibilities for managing and utilizing data around the three key data processes: Data access management, data classification, and data storage and retention.
The process of data collection must be restricted to the requirement of use cases that arises from the business goal with measurable outcomes. Organisation that require personal data must ensure written and valid customer consent is in place. for instance: if a use case requires personal data, the organization must seek and document consent from customers in line with the prevailing regulation (e.g., PDPA in Singapore)
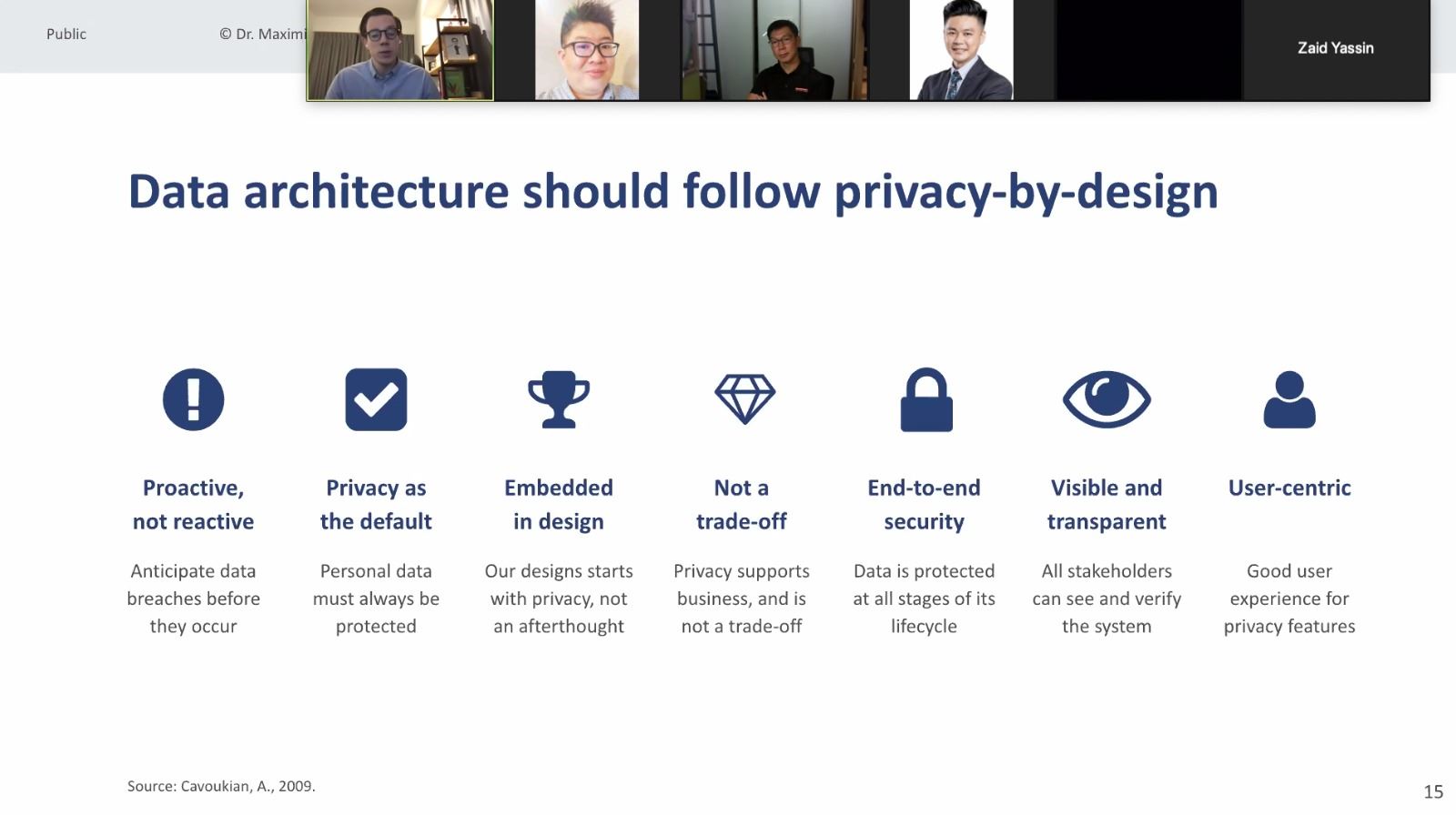
Lastly, the building blocks for your Data architectures should be built around data protection, with data privacy-by-design.
It's a great turnout and we have received raving feedbacks from audience. Dr. Max's presentation deck can be found on our members portal. Through the survey feedback, many participants appreciate the practicality of use cases over what has taken place, what was carried out, how and why did it happened. I believed its a good learning lesson for me as it is for all of you.
Thank you to our guest speaker, Dr. Max and fellow members for the participation. Join us for the next “Learning Never Stops” event brought to you by (ISC)² Singapore Chapter!
(ISC)2 Singapore Chapter MOU Signing with AISG on 28 April March 2021:



(ISC)² Singapore Chapter has signed an MoU with AISG to plus-skill our cybersecurity professionals in AI literacy and proficiency. This partnership will see us offering a series of AI webinars/seminars and clinics to help both members. We hope to build up a pool of AI savvy cyber professionals who will make a mark in the industry. Let us join our hands to combat cyber threats with game-changing innovation.

Special appreciation to our President Victor Yeo and AI SG Mr Laurence Liew for gracing the occasion and our Event Lead Louis Sin who has orchestrated the event setup. Our heartfelt thanks to the host AI Singapore for providing the nice venue and facilities. Finally, to all those who have helped in one way or another to make this a successful start of our journey. Stay tuned for more upcoming activities.
(ISC)2 Singapore Chapter LearningNeverStops Virtual Sharing #03 on 18 March 2021:
Webinar Topic: Demystifying Digital Forensic Incident Response (DFIR) Service During COVID-19 Pandemic
Speaker: Chua Zong Fu
Data breaches happen every day and Adversary will not be resting on their laurels during COVID-19 period.
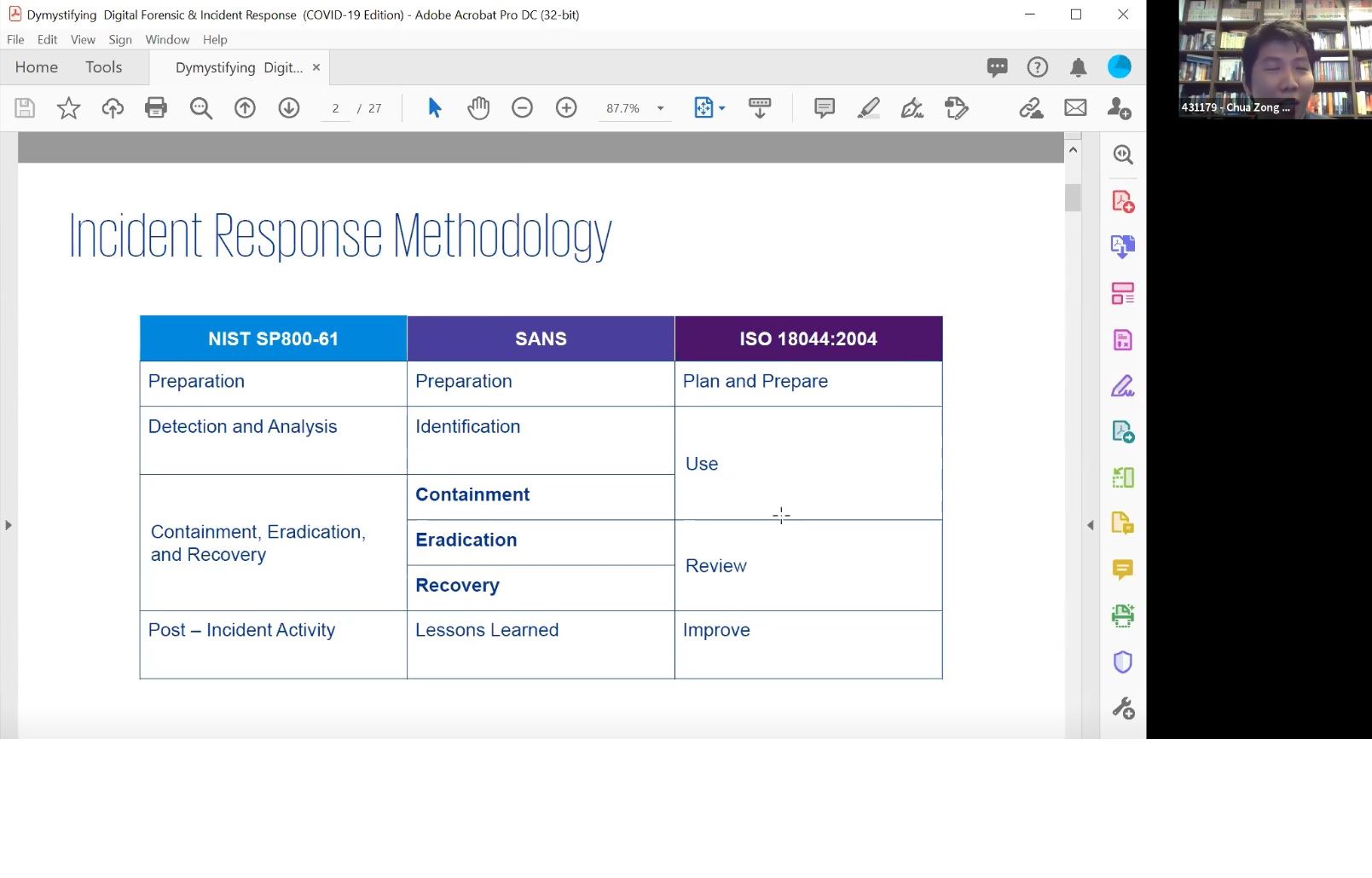
The webinar begins by introducing 6 phases of incident response and its variations across different international recognised standards such as NIST, SANS & ISO.
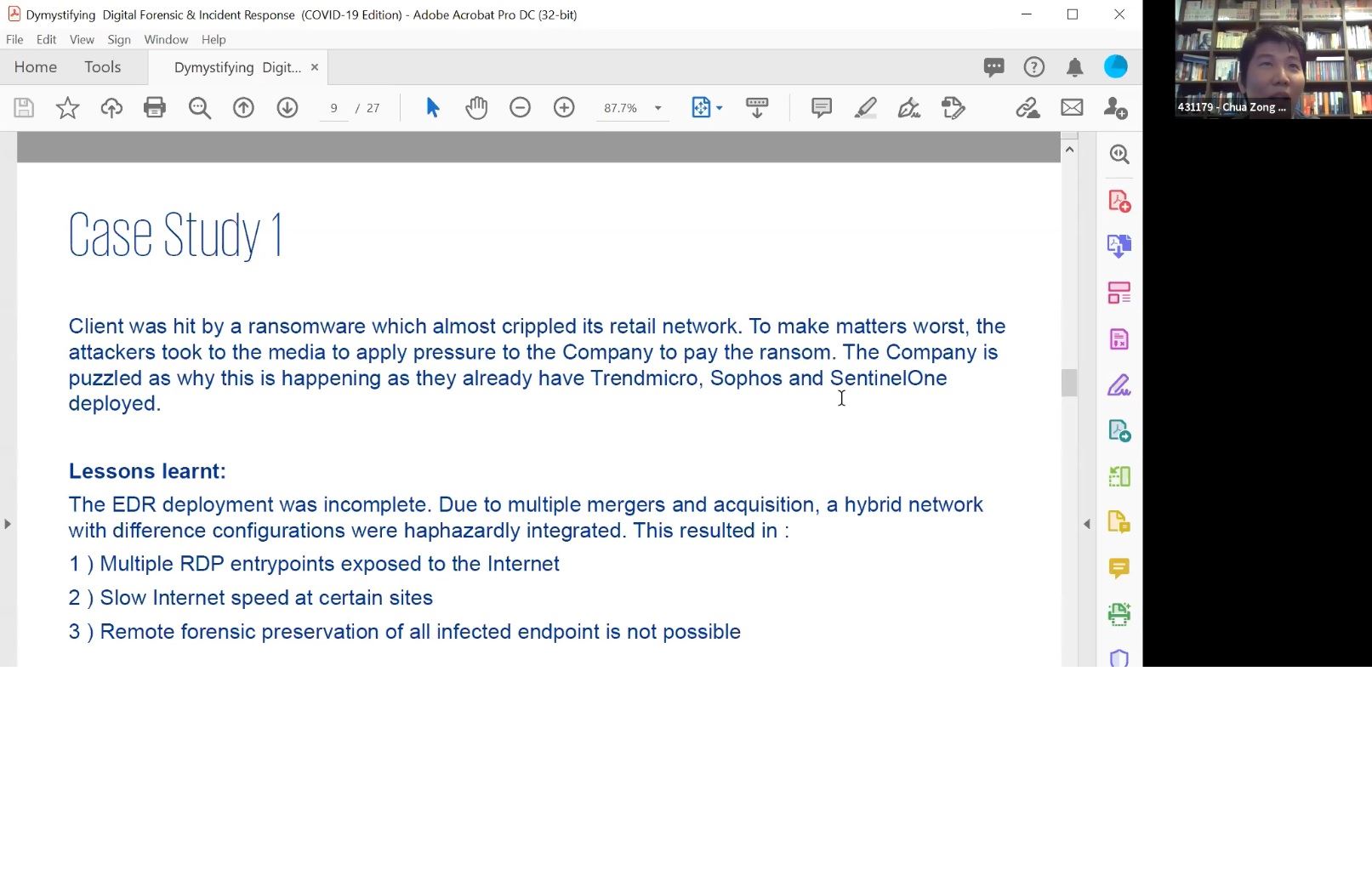
Zongfu echoed similar sentiments and challenges of fellow DFIR industry partners that COVID-19 have been consistently push the envelope of Incident Responders' reactions and force their business to revolutionise new ways of engagement delivery especially onsite evidence gathering and preservation may not be possible due to restriction of safe management measures
As an alternative measure, Zongfu describes the importance of exploring remote DFIR services and what organizations need to do prepare their environments for remote digital forensics and virtual incident response coupled with proper runbook or playbook so that security operations staff will be able to carry out tasks at ease during immerse pressure moment. Hence, checklist and automation are the key to the success!
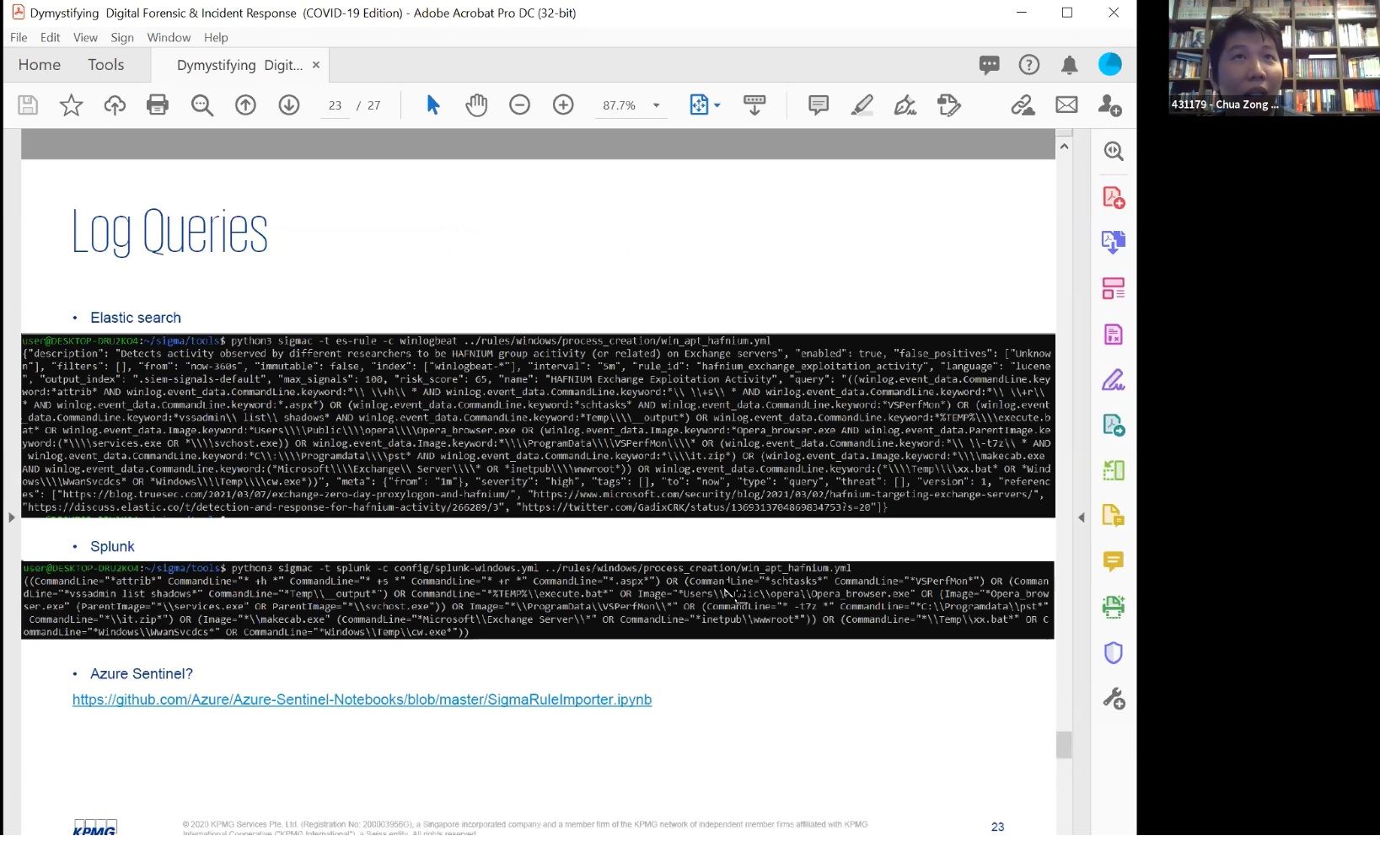
Even in a non-COVID-19 era, Incident Responders are already facing many challenges due to the wide range of security vendors (ie. EDRs, SIEMs) procured by their clients. All the logs must parsed into a common event format in order to facilitate investigation and detailed analysis.
In his presentation, Zongfu has illustrated several real-life use cases and application of forensic & analysis tools (ie. SIFT, KAPE, Encase, ELK, Azure Sentinel & etc) which are utilised heavily by his team members. All presented examples and incidents described have been anonymised to maintain & protect privacy.
Through the survey feedback, many participants appreciate the practicality of use cases over what has taken place, what was carried out, how and why did it happened. I believed its a good learning lesson for me as it is for all of you.
Thank you to our guest speaker, Mr Chua Zongfu and fellow members for the participation. Join us for the next “Learning Never Stops” event brought to you by (ISC)² Singapore Chapter!
(ISC)2 Singapore Chapter LearningNeverStops Virtual Sharing #02 on 24 Feb 2021:
Webinar Topic :Democratizing External Cyber Threat Intelligence
Speaker: Alon Arvatz
What an incredible couple of days into Year of OX as we usher our first ever "Ox-spicious webinar" with Mr. Alon Arvatz, Co-Founder and Chief Products & Strategy Officer of Intsights, hosted by Mr. Anthony Lim, Director Advocate, ExCo 2020 – 2021 of (ISC)² Singapore Chapter. Arvatz shared his thought leadership in External Cyber Threat Intelligence on market trends and complications in the marketplace, challenges organizations face today, and key considerations and recommendations for organizations to adopt an effective External Cyber Threat Intelligence.
According to Arvatz, there are misconceptions about the usage, adoption and understanding of Threat Intelligence. He spoke about the "confusing marketplace" as many information security vendors featuring the term “Threat Intelligence” on their websites. He addressed several common misunderstandings such as equating Indicators of Compromise (IoCs) with Threat Intelligence. It’s paramount to have a different mindset by gaining perspectives from an attacker’s point-of-view.
Like most users, the Internet is what we experience through social media, news channels, mobile applications, emails and web browsers every day. However, there are a large number of expansive services which operates in the background and the “web” as most users know it, is just one part of a much bigger ecosystem. Differences between Clear Web vs. Deep Web vs. Dark Web were clearly articulated.
He advised that organizations and cyber security professionals need to have a clear distinction between “Data”, “Information” and “Intelligence”; that we should strive to deliver “Intelligence” which provides more relevancy, instead of "Data" and "Information". Rather than just providing actionable intelligence, we should also be looking at providing remediation and response, by performing “take downs”. These take downs can be categorized into 2 approaches.
- External e.g. taking down malicious contents - phishing sites, fake mobile apps, GitHub codes etc.
- Internal e.g. connecting to security devices to remove threats - resetting passwords etc.
Arvatz ended his presentation by underlining the importance visualization and UX design to provide instant understanding of threats, maximize investment value, reduce overheads on security operations teams, as well as a live demo on several use cases.
Lots of questions from webinar attendees during Q&A and Alon Arvatz responded with ease and shared his experiences and point of views on how Intsights had revolutionized the cybersecurity operations with its external threat protection platform, collaborating with cyber security vendors, registrars etc.
Before we wrapped up our session, we re-visited some key takeaway messages with a fun and entertaining Kahoot Quiz Challenge.
Congratulations to all quiz winners! We will be in touch with the prizes sponsored by Intsights.
Thank you to our special guest speaker, Alon Arvatz of Intsights, sponsors, members and friends for your continuous support and making our first cyber security conference of the year 2021 an unforgettable and memorable event.
Join us for the next “Learning Never Stops” event brought to you by (ISC)² Singapore Chapter!
(ISC)2 Singapore Chapter LearningNeverStops Virtual Sharing #01 on 20 Jan 2021:
Webinar Topic :Adopting a Zero-Trust Approach in your Security Organisation in the midst of COVID-19 and SoloriGate
Speaker: Aloysius Cheang
We started our first event in 2021 addressing the topic of Zero Trust security and Solorigate - Quoted by some as "The Most Complex And Sophisticated Supply Chain Attack In History" that may potentially compromised up to 200 organizations. To address supply chain attacks, our distinguished speaker: Mr Aloysius Cheang, Chief Security Officer of Huawei Middle East, advocates the importance of implementing "Zero Trust" approach and shared an "ABC" Strategy - Assume nothing, Believe no one and Check everything. Zero Trust Security mindset should begin with stringent cybersecurity procurement policy that requires suppliers to properly qualify and share their cybersecurity process & compliance. This will ensure supplier has effective measures in place and am able to manage their security risk in their product. Strong security first or security by design architecting is needed to combat the supply chain security threats we are facing today.
During the webinar, there were many interactions between the participants and speaker, most would have gotten a couple of takeaways from the sharing to improve on their own cybersecurity posture.
Thank you all for participating. Join us at our next LearningNeverStops event.
- Home
- Events
- Upcoming and Past Events
- Events Coverage 2021